You've probably seen on social media how many experts share opinions on cybersecurity. They often mix different terms without clear explanations. In application security, for example, people sometimes ask about the difference between AppSec and DevSecOps.
This question might seem strange at first, but it makes sense because, in some situations, these terms are used interchangeably.
At first, the terms seem simple and different. AppSec is short for application security, which is a part of cybersecurity focused on making software safe. For example, “software” covers many things, and securing it can mean analyzing code, testing live applications, protecting the deployment process, and more.
In the tech world, AppSec is often mainly about finding and fixing security weaknesses in web applications.
DevOps itself is a way of working that combines application development and operations into one smooth, automated, and continuous flow. The idea of DevSecOps, or SecDevOps depending on who you talk to, came about because DevOps teams were moving faster than traditional security methods could keep up.
Automated security tools and processes needed to be added into the workflow. That’s how “Sec” became part of DevOps creating DevSecOps.
Recently, the rise of AI-generated content has made things even more confusing and noisy. To help clear things up, let's take a simple look at what AppSec and DevSecOps have in common, how they differ, and where they overlap. So we can put an end to the confusion once and for all.
Application Security, or AppSec finds, fixes, and prevents security weaknesses in software applications. It includes writing secure code, testing applications for security issues, and following rules to stay compliant.
The main goal is to lower the chances of security issues like SQL injections, cross-site scripting (XSS), broken login systems, and insecure APIs. To do this, security teams use various tools to identify and fix potential vulnerabilities. Such as:
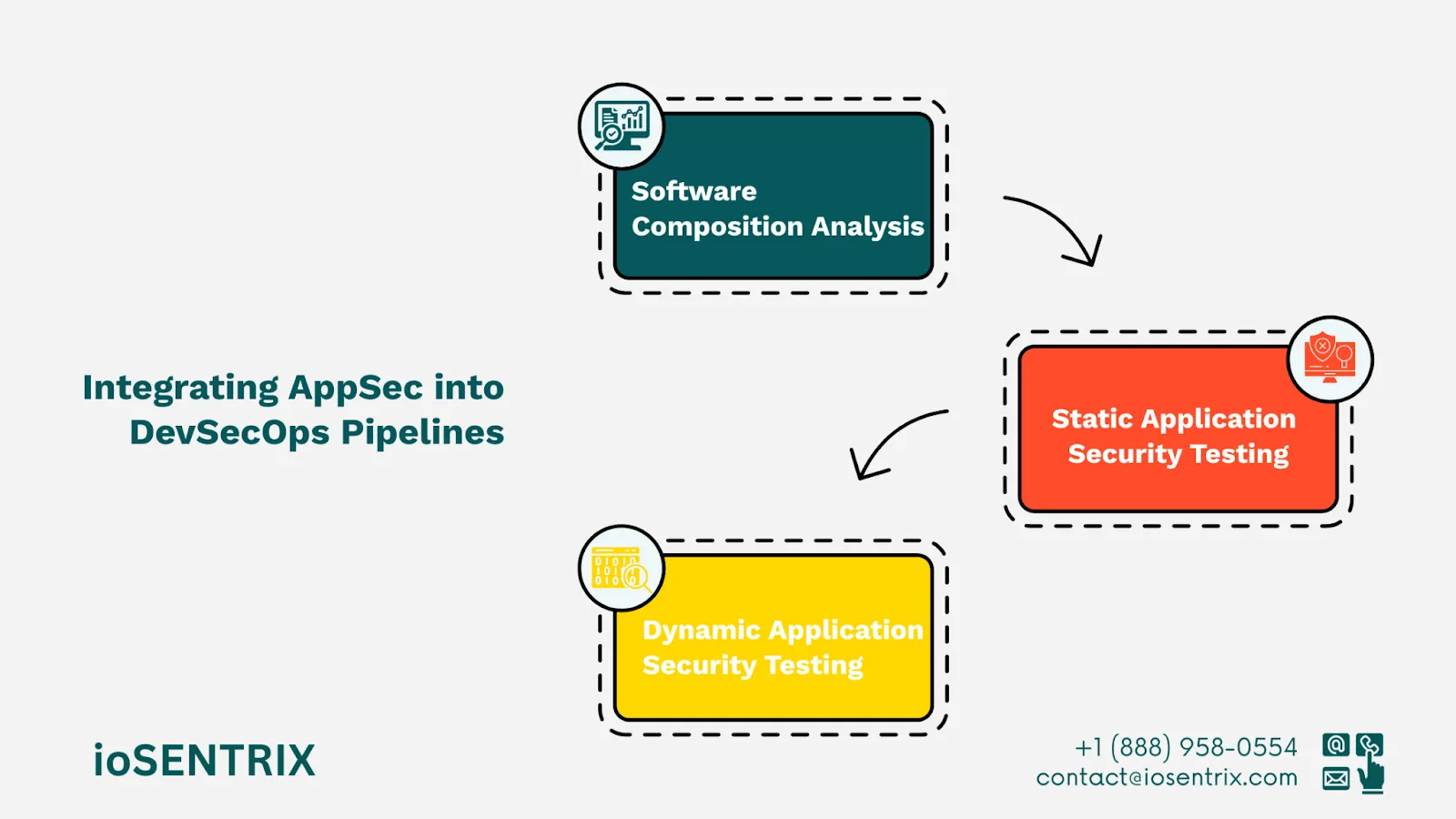
Static Application Security Testing (SAST): Checks the source code for security issues before the application is run.
Dynamic Application Security Testing (DAST): Tests the application while it is running to find security problems in real time.
Interactive Application Security Testing (IAST): Combines both SAST and DAST techniques to provide a more detailed view of security vulnerabilities.
Besides testing, AppSec also follows secure coding standards, threat modeling, and compliance requirements like PCI DSS, ISO 27001, and NIST SSDF.
Security teams collaborate with developers to make sure security is built into the application before it is launched. However, this approach addresses issues after they arise, rather than preventing them in advance.
AppSec techniques begin with a good understanding of the application, including the programming languages, frameworks, and best engineering practices. Teams use various AppSec techniques to improve security. These include:
Although AppSec is still an important part of software security, today’s development processes need a more connected method. That’s where DevSecOps becomes a part of the entire development cycle.
DevSecOps is a way of working that changes how teams operate and think. It brings security into DevOps from the very beginning. Instead of handling security as a separate step, DevSecOps makes security a shared task for developers, security experts, and operations teams.
The main idea of DevSecOps is “shifting security left,” which means including security measures early in the software development process. This approach helps teams find and fix risks more quickly, reduces delays caused by security issues, and makes it easier to stay compliant.
DevSecOps depends a lot on automation and ongoing security checks to smoothly include security into the CI/CD pipelines. Some important tools that help with security automation in DevSecOps include:
Software Composition Analysis (SCA): Checks open-source dependencies for any security issues.
Container and API Security: Focuses on monitoring and securing microservices and their connections.
Infrastructure as Code (IaC) Security: Makes sure that cloud setups and infrastructure are secure and protected from attacks.
It’s important that security is integrated from the beginning, rather than being an afterthought or just the responsibility of one team. A good security program involves different people working together smoothly, like a well-coordinated dance, to keep everything secure throughout the development process.
In a DevSecOps approach, several techniques are commonly used to enhance security. These include:
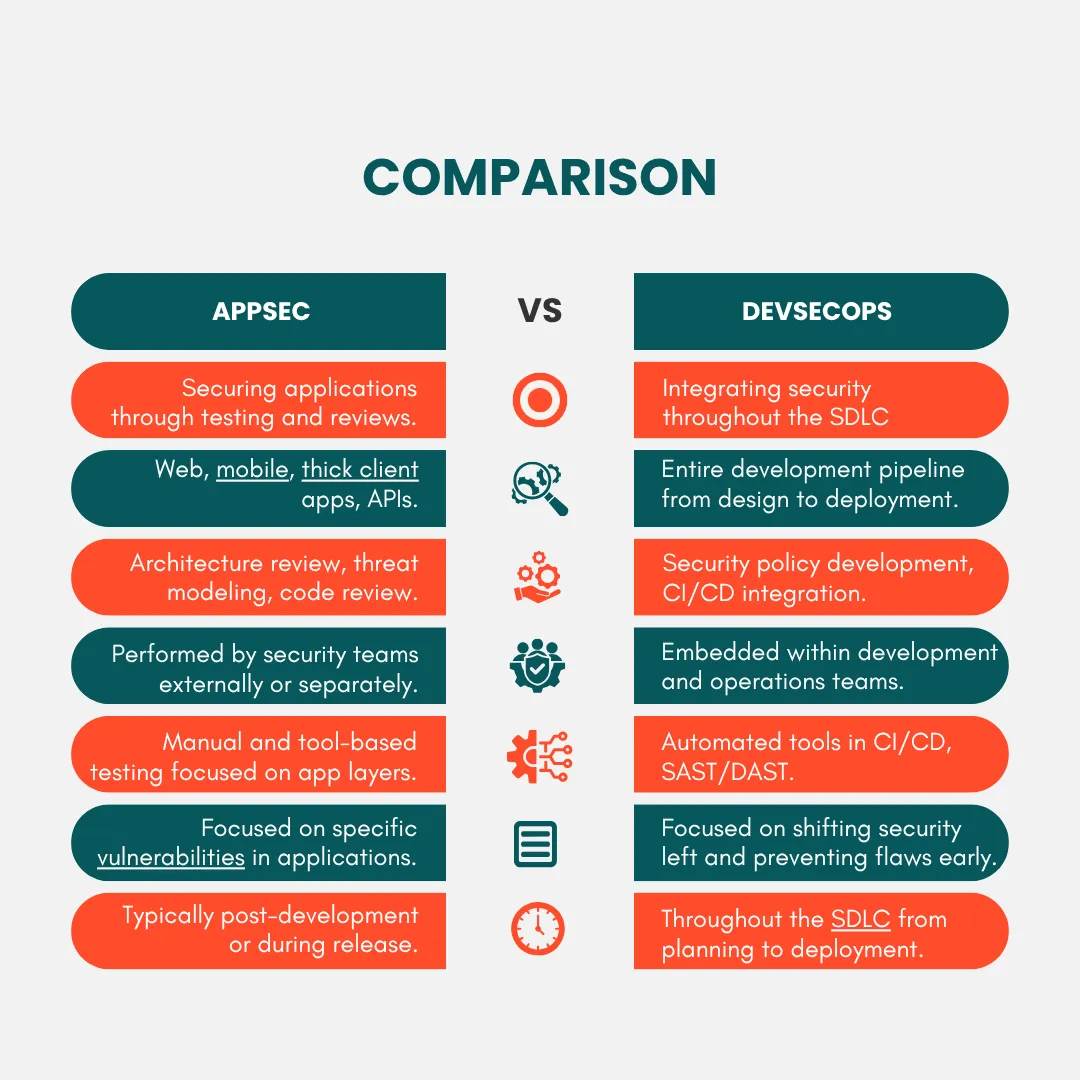
While both Application Security (AppSec) and DevSecOps make software safer, they have different focus areas and methods. AppSec mainly focuses on protecting specific applications by testing and secure coding practices.
On the other hand, DevSecOps incorporates security into every stage of the software development process. It uses automation and monitoring to ensure security is a continuous part of building and maintaining software.
Here is a concise comparison table highlighting the key differences between Application Security and DevSecOps services as provided by ioSENTRIX:
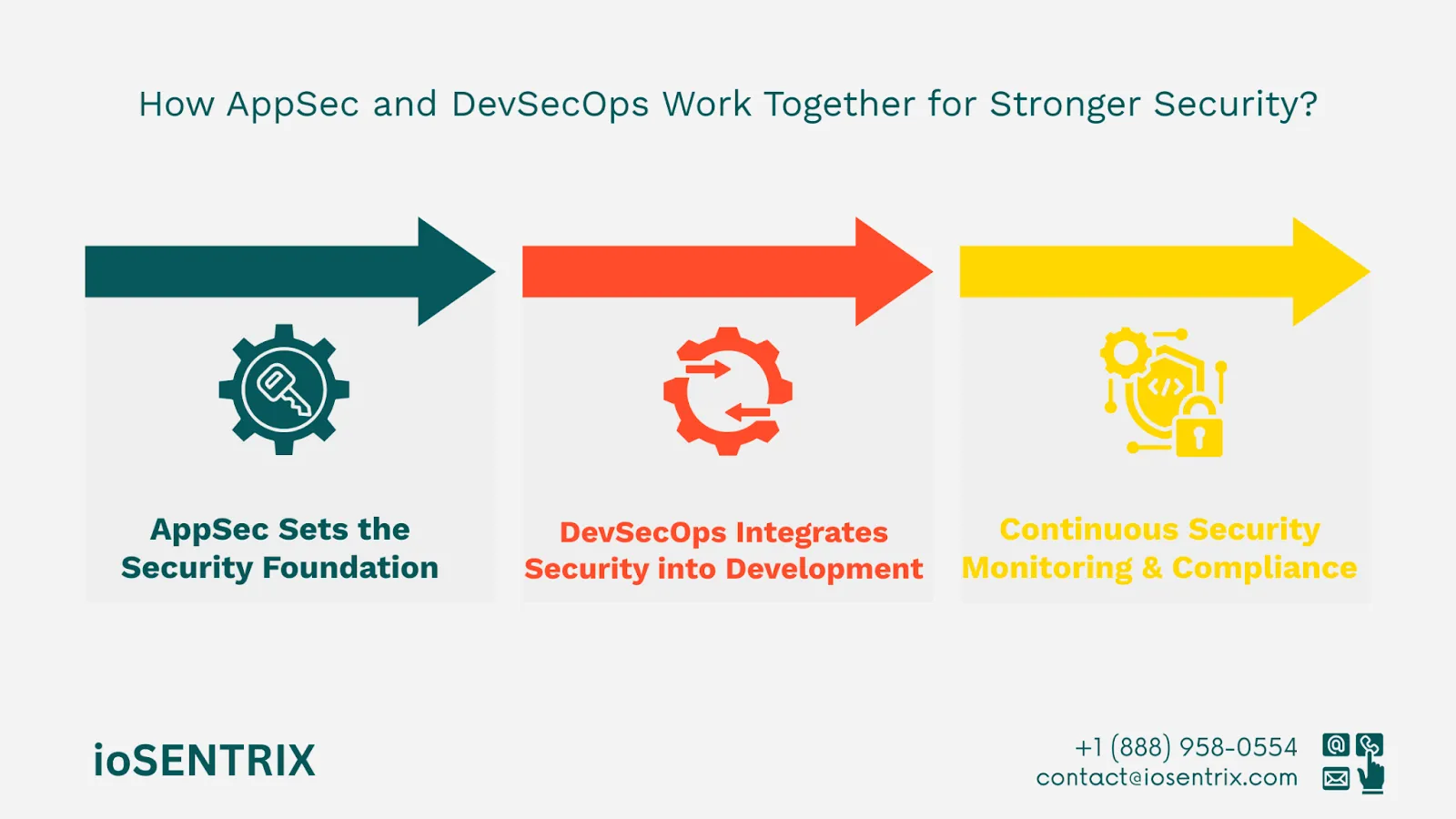
Although AppSec and DevSecOps focus on different areas, they work well together to build a strong security approach for software. AppSec offers the basic building blocks, like secure coding, testing for vulnerabilities, and meeting compliance standards.
Meanwhile, DevSecOps makes sure security is part of every step in the software development process. Together, they help create a more secure and reliable software environment.
Here's how AppSec and DevSecOps work together:
The idea of including security as part of software quality sounds good in theory, but in reality, development teams often find working with security challenging. This is especially true with the shift to agile DevOps, which involves quick, frequent releases in short cycles.
When security teams or external testers identify issues weeks later, it can be frustrating and slow down the continuous integration and delivery process. That’s why when people talk about DevSecOps tools, they usually mean security tools that can work smoothly within the DevOps workflow without disturbing the team's progress.
There are three main ways to perform automated and continuous security testing for applications in the DevOps process. These include two static methods, SAST and SCA, and one dynamic method, DAST.
Each method has its own benefits and some limitations. To get the best results, it's recommended to use all three at different points in the development process.
SCA solves the issue of heavy dependence on open-source software components. These ready-made parts and frameworks allow developers to follow standards and spend more time on custom features that are unique to their business.
SCA helps identify and update known vulnerable components or avoid using them altogether. Some SCA tools also check for license compliance and scan code for open-source snippets. However, one challenge with SCA is that it can produce many warnings that aren’t relevant to the specific project.
Developers may need to filter out or ignore these alerts to focus on what’s more important.
The most common way to add security checks during development is to scan the code for vulnerabilities right after it is written. This is similar to how linters and other development tools are used to find coding mistakes.
SAST tools can be used directly in the IDE or run separately as an analysis process. The benefit is that these tools easily fit into the software development lifecycle and can be used at any stage, even on code that isn’t yet ready to run or isn’t part of the live application.
Like SCA, one of the main challenges with SAST is that it can generate a lot of false alarms or warnings that are correct but not relevant. Since SAST is a static analysis, it can’t tell if a reported issue will actually be exploitable in real life.
It also can’t detect vulnerabilities that happen during runtime, which may come from configuration issues or external dependencies.
DAST tools have grown beyond their traditional role as external vulnerability scanners to also perform dynamic testing during quality assurance. DAST can scan any web application or API that can run, including prototypes, regardless of the technologies used.
High-quality DAST tools tend to have very few false alarms and are easier to set up and tune compared to SAST. They also work well with popular issue trackers and collaboration tools. Security issues can be sent directly to developers along with guidance on how to fix them.
DAST tests only the parts of an application that are running. Any code that isn’t loaded during testing won’t be checked. DAST also can’t test static code, like individual snippets or modules, and sometimes it shows slightly less precise locations for issues compared to SAST, which can point directly to specific lines of code.
The quality and usefulness of DAST results can vary a lot depending on the tool you choose. A good DAST tool can be a key part of your DevSecOps process. However, a less reliable DAST may cause more problems than it solves and might not be worth using.
AppSec and DevSecOps are closely connected and share many similarities. However, most large organizations develop some of their software in-house, which creates an overlap between the two.
All the different terms and buzzwords basically mean having a regular, continuous process to keep software secure.
This process begins with designing and coding securely, then moves on to automated testing to find security issues, and finally involves maintaining a strong security posture while the software runs in production. The name or labels don’t matter as much as using the right tools and practices to manage security risks effectively.
AppSec is about protecting individual applications by checking for vulnerabilities, promoting secure coding habits, and following compliance standards. DevSecOps, on the other hand, makes sure that security is part of the work from start to finish, with regular security checks throughout the entire development cycle.
Application security, or AppSec, includes the methods, practices, and tools used to find, fix, and defend against weaknesses in software. This process is applied at every stage of the software development life cycle to help keep applications safe.
DevSecOps is a way of including security in application development from the very beginning. It brings security practices into the early stages of the software development life cycle. Safety thus becomes an integral part of the process.
DevSecOps brings together the three key areas of software development: development, security, and IT operations. It is an extension of DevOps, which focused on aligning development and operations, but kept security separate and outside the main process. DevSecOps integrates security into the entire development and operations workflow for a more secure and efficient approach.
By 2025, application security will focus on proactive steps, tools that understand the context, and smooth teamwork. Companies that put effort into clear visibility, automation, and secure development methods will be better prepared to defend their applications.