
AppSec engineers play an important role in modern cybersecurity teams. They bridge the gap between developers and security operations by embedding security into every phase of the software development lifecycle. They are responsible for conducting threat modeling, code reviews, automated security testing and managing vulnerabilities.
An Application Security (AppSec) Engineer is a specialized cybersecurity professional focused on safeguarding software applications against security vulnerabilities and cyber threats. Unlike traditional software developers, AppSec engineers are responsible for integrating security into every phase of the Software Development Life Cycle (SDLC), from initial design and architecture to deployment and maintenance.
Their core responsibilities include:
While all three roles contribute to a secure tech ecosystem, their focus areas and skill sets differ:
AppSec engineers evaluate application designs and system architectures to identify and mitigate structural security flaws before development begins. They assess components, data flows, and third-party integrations to ensure a security-by-design approach.
Threat modeling helps AppSec engineers anticipate how attackers might exploit a system and identify weak points in the application. They assign risk levels to potential threats and help prioritize remediation strategies based on business impact.
AppSec engineers perform code reviews using both automated tools and manual inspection to detect issues like insecure input validation, authentication bypasses, or cryptographic misconfigurations. This helps catch implementation flaws that traditional QA processes may overlook.
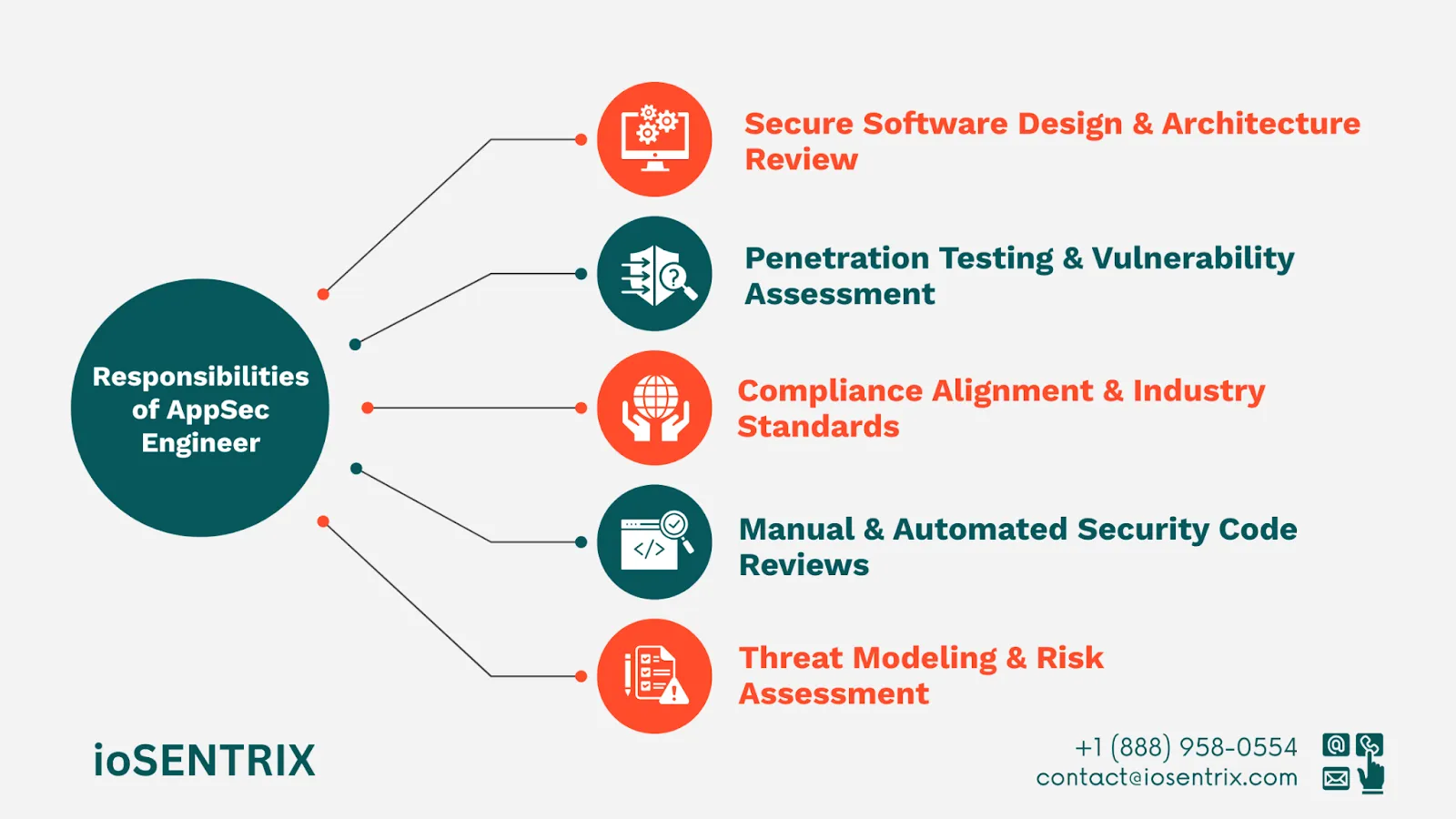
Beyond code, AppSec engineers execute application-level penetration testing to simulate real-world attack scenarios. They uncover exploitable vulnerabilities and provide detailed remediation guidance to harden applications against both automated and targeted attacks.
To meet regulatory requirements, AppSec engineers map security measures to compliance frameworks such as PCI DSS, HIPAA, FFIEC, and GDPR. Their work helps ensure that applications are not only secure but also audit-ready.
A successful Application Security (AppSec) Engineer possesses a unique blend of development expertise, security acumen, and communication skills. This specialized role requires the ability to secure modern software applications while collaborating with development teams, DevOps, and business stakeholders.
Below are the key skills and qualifications that define a top-tier AppSec engineer:
A deep understanding of programming languages like Java, Python, C#, or JavaScript is required. AppSec engineers must be able to read and analyze code efficiently, identify security flaws, and guide developers in writing secure alternatives. A background in full-stack or backend development is especially valuable.
Knowing how to code securely is fundamental. AppSec engineers must be well-versed in secure software development principles, including input validation, access control, encryption, and session management. They serve as advocates for secure coding across the SDLC.
To assess and prioritize risks accurately, AppSec engineers must have expert knowledge of:
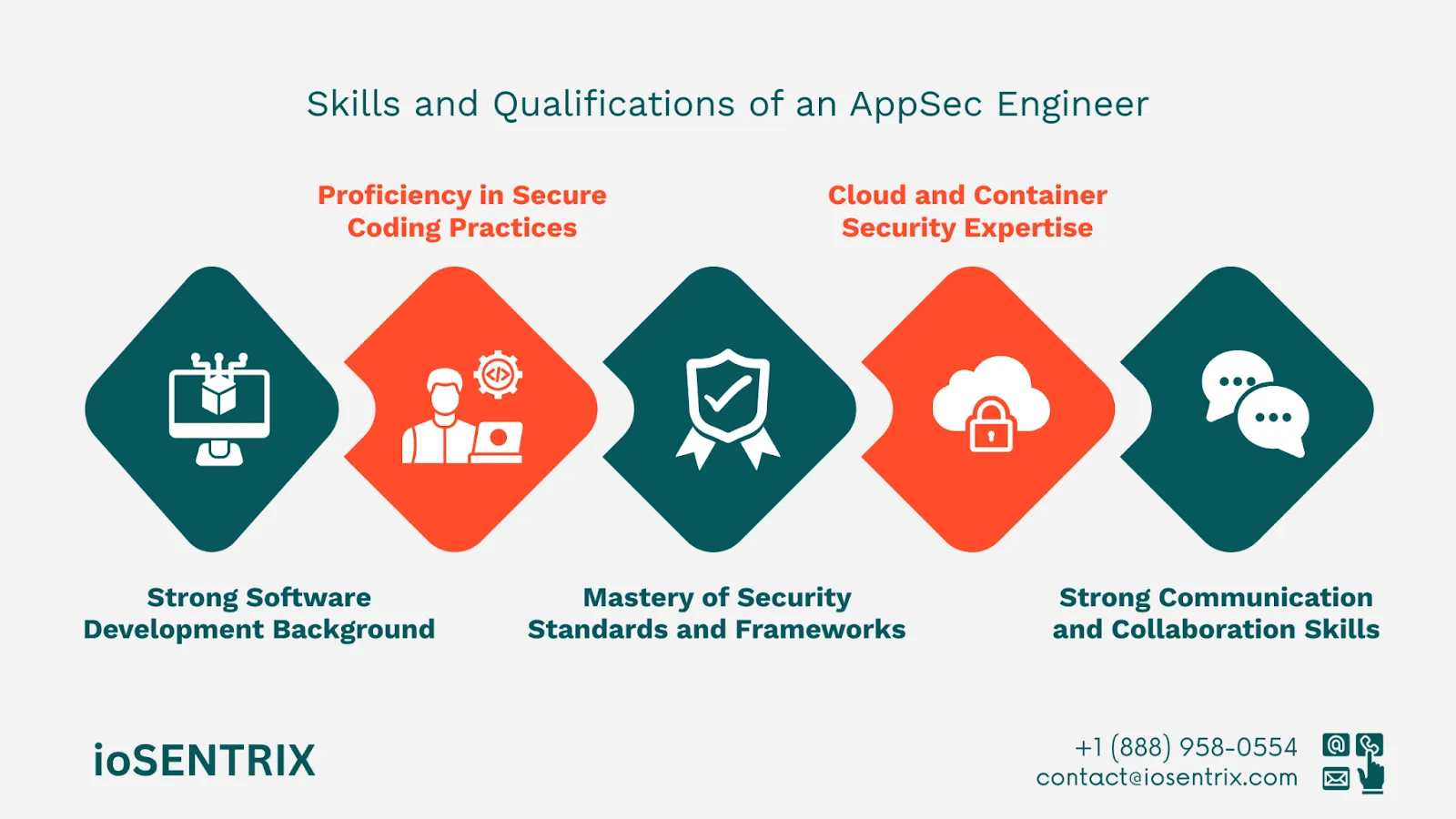
With the shift toward cloud-native development, AppSec engineers must understand the security models of platforms like AWS, Azure, and GCP, as well as container ecosystems (e.g., Docker and Kubernetes). Their role includes securing APIs, storage buckets, serverless functions, and container images.
AppSec engineers act as liaisons between security, development, and business teams. Excellent written and verbal communication skills are vital for:
Security must be considered from the very beginning. AppSec engineers collaborate with product owners and business analysts to define security requirements alongside functional ones. This approach ensures that compliance, data privacy, and threat mitigation are built into the application’s foundation.
Key activities:
During the design phase, AppSec engineers perform threat modeling to identify potential attack vectors based on the application’s structure and data flows. They also assess the architecture to ensure it adheres to security-by-design principles.
Key activities:
As development progresses, AppSec engineers provide guidance on secure coding practices and perform static application security testing (SAST). They also conduct manual and automated code reviews to detect and eliminate vulnerabilities like injection flaws or insecure dependencies.
Key activities:
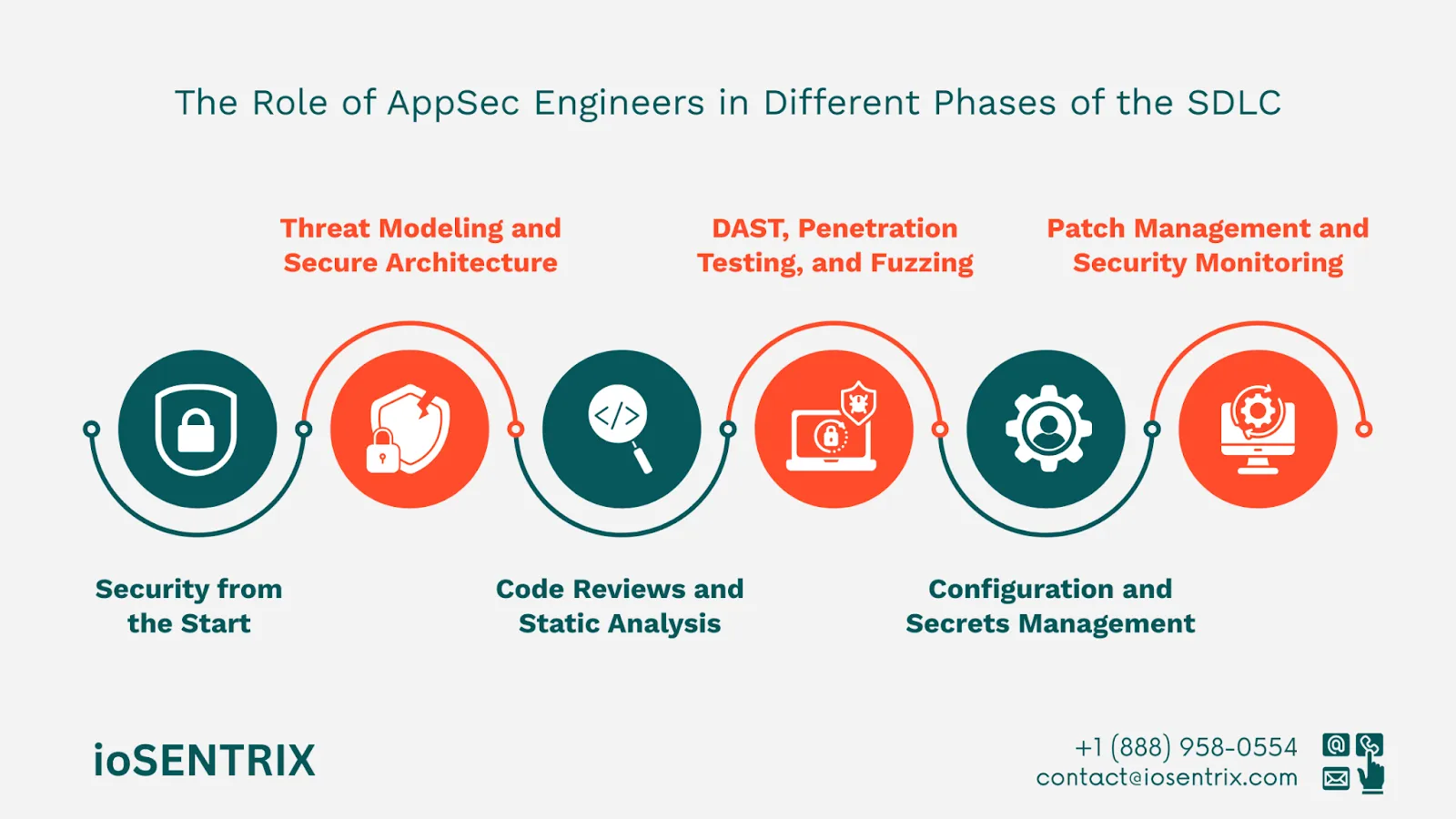
Before release, AppSec engineers assess the application’s security through dynamic application security testing (DAST) and penetration testing. They may also use fuzz testing to uncover unexpected behavior and crashes under malformed inputs.
Key activities:
At deployment, AppSec engineers ensure secure configuration of environments, proper access controls, and secure handling of secrets and API keys. They work closely with DevOps to maintain security in containerized and cloud-based environments.
Key activities:
Post-deployment, AppSec engineers monitor for new threats, ensure timely patching, and support security operations in tracking anomalies. Continuous assessment helps maintain a strong security posture throughout the application’s lifecycle.
Key activities:
AppSec professionals typically begin their careers in entry-level cybersecurity or software development roles, such as:
With experience and technical maturity, professionals can progress to advanced roles like:
AppSec engineers have the flexibility to branch out into specialized domains based on interest and industry needs. Popular specialization areas include:
To validate their skills and stand out in the job market, many AppSec professionals pursue industry-recognized certifications. Highly respected options include:
There’s constant pressure to deliver software quickly. AppSec engineers must embed security into agile workflows without slowing down releases. Striking this balance between speed and security is one of the biggest challenges.
Key issues include:
Automated security tools such as SAST, DAST, and dependency scanners often generate a high volume of alerts, many of which are false positives. Sifting through these to identify real threats can lead to alert fatigue, causing critical issues to be overlooked.
Challenges include:
AppSec engineers frequently collaborate with developers, DevOps teams, QA engineers, and product managers. Explaining complex security risks in a way that resonates with non-security stakeholders can be difficult.
Communication challenges include:
Collaboration between AppSec engineers, penetration testers, and red teams is necessary for end-to-end application security. While their roles differ in scope and timing, these professionals work in tandem to identify, validate, and remediate security vulnerabilities across the application landscape.
Penetration testers simulate attacks to uncover exploitable vulnerabilities in live or pre-production environments. Their goal is to assess the effectiveness of security controls and coding practices already implemented by AppSec engineers.
AppSec-Pentester collaboration includes:
Red teams simulate advanced, persistent threat scenarios that mimic real-world attackers. Their tests go beyond vulnerability discovery to assess an organization’s detection and response capabilities across the entire attack surface.
AppSec engineers benefit from red team exercises by:
AppSec engineers serve as both guardians and enablers of innovation. Their expertise ensures that security is not a barrier to development but a strategic advantage. This future demands AppSec professionals who can:
The future of application security lies in intelligent, adaptive security engineering and AppSec engineers will lead the charge.
Looking to assess or improve your application security posture? Contact ioSENTRIX to speak with an expert and request a customized AppSec strategy.
The main job of an Application Engineer is to create and enhance software to meet specific needs. They work closely with clients to understand their unique goals and requirements for each project. After careful evaluation, they plan and implement solutions that fit those needs.
Application Security Engineers bring a special set of skills in both coding and cybersecurity. Their job is to make sure that applications not only function properly but are also secure from potential threats. This helps create safer and more reliable software for everyone.
Successful AppSec engineers need a strong background in software development (e.g., Java, Python), deep knowledge of secure coding practices, and familiarity with security standards like OWASP Top 10, CVSS, CWE, and CAPEC. They must also understand cloud security, containerization (e.g., AWS, Docker), and possess excellent communication skills to collaborate with cross-functional teams.
While software developers focus on building functional and user-friendly applications, AppSec engineers prioritize embedding security throughout the development process. Unlike ethical hackers or penetration testers, AppSec engineers work within the SDLC to prevent vulnerabilities.