Cybersecurity has become a critical concern for organizations of all sizes. With more advanced and frequent threats, the demand for strong cybersecurity leadership has intensified. Companies, whether small startups or large enterprises, recognize that effective security management is essential to protect sensitive data, maintain customer trust, and ensure regulatory compliance.
However, many organizations face challenges in recruiting, hiring, and retaining experienced Chief Information Security Officers (CISOs), often due to resource constraints or the evolving complexity of cybersecurity threats.
To address this gap, the concept of virtual Chief Information Security Officers (vCISOs) has gained considerable traction. vCISOs offer a flexible, and cost-effective alternative to traditional, full-time security leadership.
They enable organizations to access expert cybersecurity guidance without the overhead costs associated with a full-time executive. This model allows businesses to match security strategies to their specific needs, regardless of size or industry.
A virtual Chief Information Security Officer (vCISO) is an outsourced cybersecurity professional or service provider that delivers executive-level security leadership and strategic guidance without the need for a full-time, in-house hire. This flexible approach allows organizations of all sizes to access advanced cybersecurity expertise on a scalable basis, often customized to their specific needs and budget constraints.
You may want to read: vCISO vs In-house CISO: Which is Better for Your Business?
Most traditional vCISO services operate on a retainer basis, often involving limited hours per month and periodic engagement points such as monthly or quarterly meetings. This flexible structure enables organizations to receive continuous security oversight without the expense and commitment of a full-time executive, making it an attractive option for growing companies or those seeking expert guidance without long-term staffing commitments.
Many traditional vCISO services adopt a standardized framework that may not fully address the unique needs and challenges of each organization. This "one-size-fits-all" approach can result in generic security strategies that lack customization, potentially overlooking specific vulnerabilities or business objectives. As a consequence, organizations might not achieve optimal security or strategic alignment with their operational goals.
While vCISOs provide valuable strategic guidance, their involvement often remains at a high level, with limited direct access to day-to-day operations. This can lead to gaps in visibility into the organization’s real-time security environment. vCISOs typically do not engage in hands-on technical implementation, which may delay the resolution of certain security issues or prevent rapid adaptation to emerging threats.
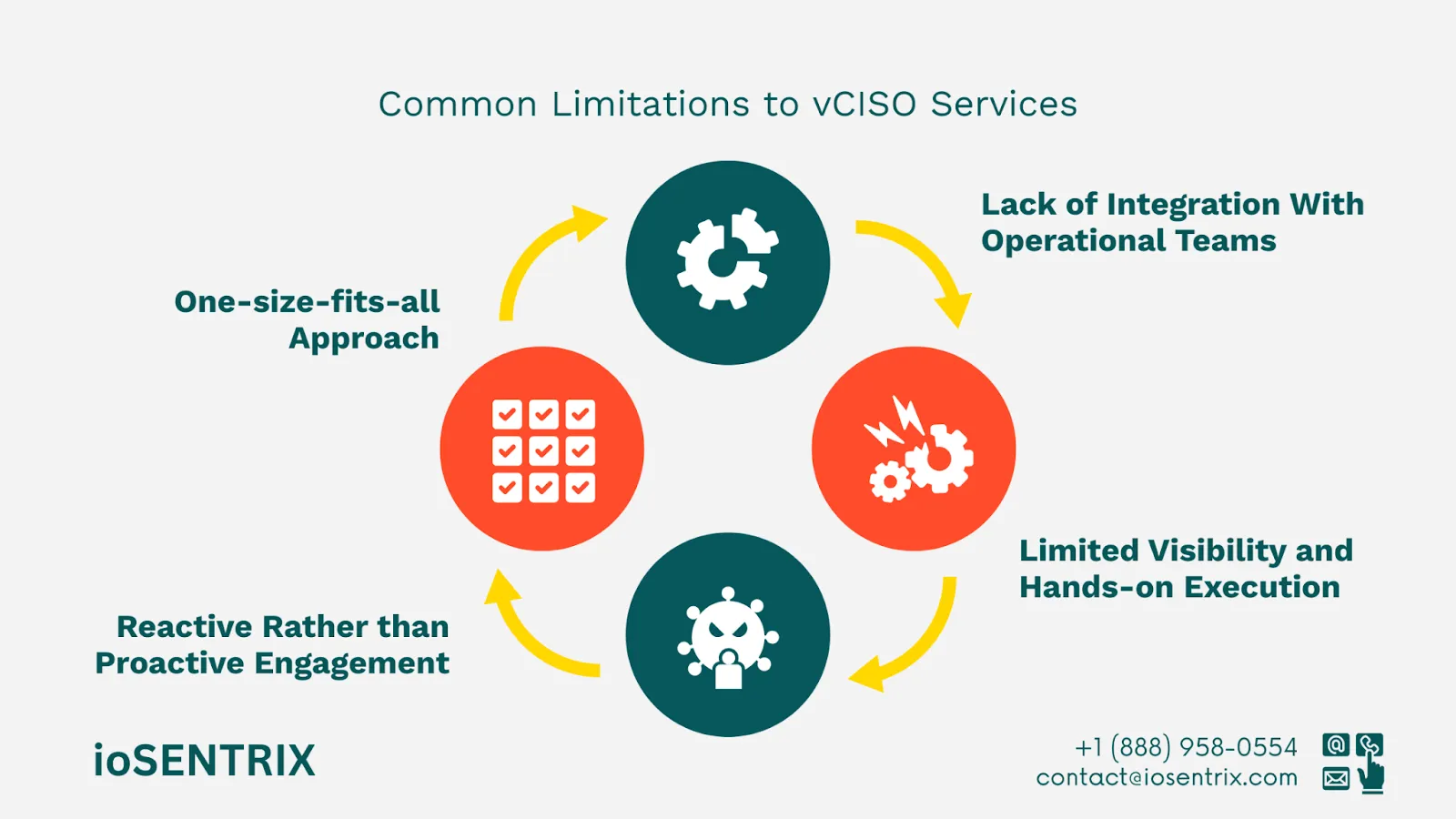
Many vCISO services tend to focus on responding to incidents or compliance requirements after they arise. This reactive approach can leave organizations vulnerable to new threats that require measures such as continuous monitoring, threat hunting, and vulnerability management. Without a proactive stance, organizations may find themselves continually firefighting rather than preventing security breaches before they occur.
Effective cybersecurity requires close collaboration between the vCISO and various operational teams within the organization. However, some vCISO models operate in silos, and lack seamless integration with IT, security, and business units. This disconnect can hinder the implementation of security initiatives, reduce overall efficacy, and create communication gaps that compromise the organization’s security posture.
One of the most defining aspects of ioSENTRIX’s vCISO service is its customized, risk-based methodology—a sharp contrast to the often generic, one-size-fits-all approach of traditional vCISO offerings.
At ioSENTRIX, every engagement begins with a deep understanding of the organization’s unique business model, regulatory environment, and security maturity. Rather than applying a static framework or relying solely on industry checklists, we design customized security programs that are specifically aligned to your organization’s operational needs and strategic objectives.
ioSENTRIX places a strong emphasis on quantifying security performance and risk reduction over time. Clients receive clear, data-driven insights into the impact of their security investments—such as reduction in vulnerabilities, improved incident response readiness, and enhanced compliance measures.
This risk-based, customized approach guides organizations not just to meet minimum security requirements, but to build lasting resilience and competitive advantage.
While many traditional vCISO services operate at a high level, ioSENTRIX takes a fundamentally different approach by embedding deep technical capabilities into every vCISO engagement.
ioSENTRIX’s model operates on a smooth integration between strategic leadership and technical execution. Each vCISO is backed by a dedicated team of cybersecurity engineers, penetration testers, and security analysts who are actively involved in day-to-day security operations and technical assessments.
Instead of simply advising on best practices, the ioSENTRIX vCISO can lead or directly support technical initiatives such as vulnerability management, incident response drills, secure architecture reviews, and cloud security posture assessments. This tight alignment between strategy and operations enables faster remediation, more effective risk mitigation, and stronger overall security posture.
The result is a truly embedded partnership, where the vCISO is not just a part-time advisor, but a dynamic member of your team.
With ioSENTRIX, organizations benefit from a cybersecurity leader who understands the business, speaks the language of the boardroom, and can also roll up their sleeves to work alongside engineers, DevOps teams, and IT administrators.
Traditional vCISO services often follow a limited engagement format: a fixed number of hours per month, quarterly check-ins, and templated deliverables. This periodic and reactive model can leave organizations with gaps in coverage, delayed decision-making, and a lack of continuous strategic momentum.
In contrast, the ioSENTRIX vCISO model is built on continuous, high-touch engagement. Rather than operating as a detached consultant, the ioSENTRIX vCISO becomes an integrated and responsive part of your leadership and operations teams. From day one, the vCISO establishes regular communication cadences—whether through weekly meetings, real-time collaboration platforms, or executive reporting sessions.
Whether your organization is facing an active security incident, preparing for an audit, or undergoing a rapid cloud migration, the ioSENTRIX vCISO is there—not weeks later, but right when it matters most.
Ultimately, this engagement style creates a sense of shared accountability and proactive collaboration, rather than a transactional service relationship. It’s this level of consistency, presence, and partnership that sets ioSENTRIX apart from conventional vCISO providers.
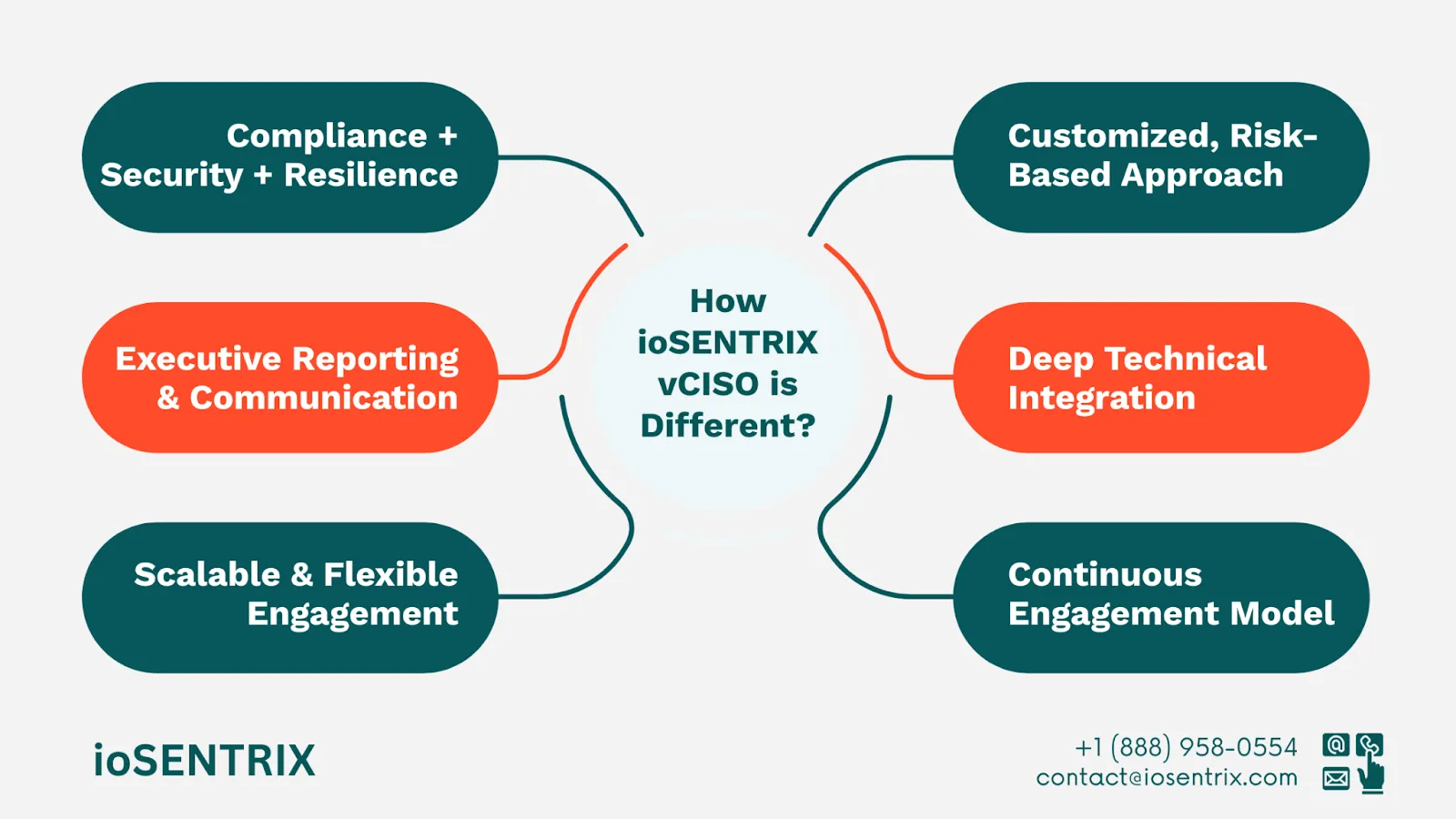
Many traditional vCISO providers tend to place heavy emphasis on compliance checklists and regulatory frameworks. While regulatory compliance is essential, it does not automatically equate to effective security or operational resilience.
ioSENTRIX goes beyond compliance by integrating three critical dimensions into every vCISO engagement:
Compliance
Security
Resilience
First, ioSENTRIX ensures that your organization meets relevant regulatory and industry standards such as HIPAA, PCI-DSS, SOC 2, and ISO 27001. But instead of merely focusing on documentation and audits, the vCISO team ensures that compliance is mapped to real, enforceable security controls.
Second, ioSENTRIX prioritizes security effectiveness by identifying actual gaps in your defenses through penetration testing, vulnerability scans, threat modeling, or architecture reviews. These activities find issues that compliance checks often miss to build a more accurate picture of your security posture.
Third, and perhaps most critically, ioSENTRIX helps organizations build resilience against incidents. This includes developing incident response plans, running tabletop exercises, simulating attacks, and ensuring your team is trained and equipped to act decisively during a crisis.
One of the common shortcomings of traditional vCISO services is their limited ability to communicate effectively across all levels of the organization. Reports are often overly technical for executives, or too high-level for technical teams.
ioSENTRIX addresses this gap with a strong focus on executive reporting and stakeholder communication.
The ioSENTRIX vCISO acts as a bridge between security operations and business leadership to translate complex technical issues into clear, actionable insights that resonate with C-suite executives, boards of directors, and non-technical stakeholders.
These communications provide strategic visibility into the organization's risk measures, security performance, and ROI on cybersecurity investments.
Deliverables such as dashboards, KPIs, board reports, and risk heatmaps are customized to each audience to help decision-makers understand:
At the same time, ioSENTRIX maintains regular technical reporting and engagement with IT, DevOps, and security teams to ensure that strategic objectives align with day-to-day operations. This dual-track communication style ensures clarity, cohesion, and accountability across all levels of the organization.
Cybersecurity is not static—it must evolve with the business. As organizations grow, enter new markets, or face shifting regulatory landscapes, their security needs also change. Unfortunately, many traditional vCISO models are rigid and limited in scope, often with fixed service packages that don’t scale easily with business complexity.
ioSENTRIX takes a different approach and offers a scalable and flexible vCISO engagement model to grow and adapt alongside your organization.
Whether you're a startup preparing for your first SOC 2 audit, a mid-market firm expanding internationally, or an enterprise undergoing digital transformation, ioSENTRIX matches its services to your current stage of maturity—and scales as your needs evolve.
You’re not locked into a static level of service; instead, you can adjust engagement levels, introduce new focus areas (like cloud security or third-party risk), or ramp up resources as the business demands.
This modular, on-demand structure allows for:
While traditional vCISO services offer basic strategic guidance, they often fall short in areas like real-time responsiveness, technical depth, and long-term integration. These limitations can leave businesses vulnerable and ill-equipped to adapt to a dynamic threat landscape.
ioSENTRIX breaks that mold with a modern, full-spectrum vCISO solution that is:
This is not just a vCISO—it’s a cybersecurity partnership designed to help your organization lead with confidence, comply with certainty, and respond with resilience.
If you're ready to move beyond conventional security models and invest in a next-generation cybersecurity leadership experience, we invite you to explore ioSENTRIX’s vCISO services.
Contact us today to schedule a consultation and discover how ioSENTRIX can help you build a smarter, stronger, and more secure future.