SOC 2 compliance has become one of the most important standards for organizations that handle customer data.
Developed by the American Institute of CPAs (AICPA), SOC 2 ensures that companies protect sensitive information through security, availability, confidentiality, processing integrity, and privacy.
These principles form the SOC 2 Trust Services Criteria and are essential for building credibility with clients and stakeholders.
Meeting SOC 2 requirements goes beyond writing security policies. Organizations must show that their controls actually work.
This is where SOC 2 penetration testing plays a critical role. By simulating real-world attacks, penetration testing validates whether the safeguards in place are effective.
With ioSENTRIX Penetration Test as a Service (PTaaS), organizations gain a reliable solution that is strategically aligned with SOC 2 security testing. It provides audit-ready deliverables, remediation insights, and ongoing validation that strengthen security and streamline the compliance process.
SOC 2 is a framework that demonstrates an organization’s ability to manage customer data responsibly.
Achieving SOC 2 compliance assures customers that a business operates with strong data protection practices. The framework is particularly relevant to SaaS providers, fintech companies, and healthcare organizations where data handling is critical.
While SOC 2 audits primarily focus on reviewing documented policies and implemented controls, auditors also expect proof that these controls work effectively. Penetration testing for SOC 2 compliance provides this proof by actively uncovering weaknesses before they can be exploited.
For Type II audits, which evaluate controls over a longer observation period, penetration testing becomes even more valuable. It offers tangible evidence that the controls remain effective during day-to-day operations.
Penetration testing aligns with SOC 2 security testing in several important ways. It ensures that organizations are not just compliant on paper but resilient against real threats.
The testing process simulates cyberattacks to highlight gaps in system security, user access, and network defenses.
Some of the key ways penetration testing supports SOC 2 compliance include:
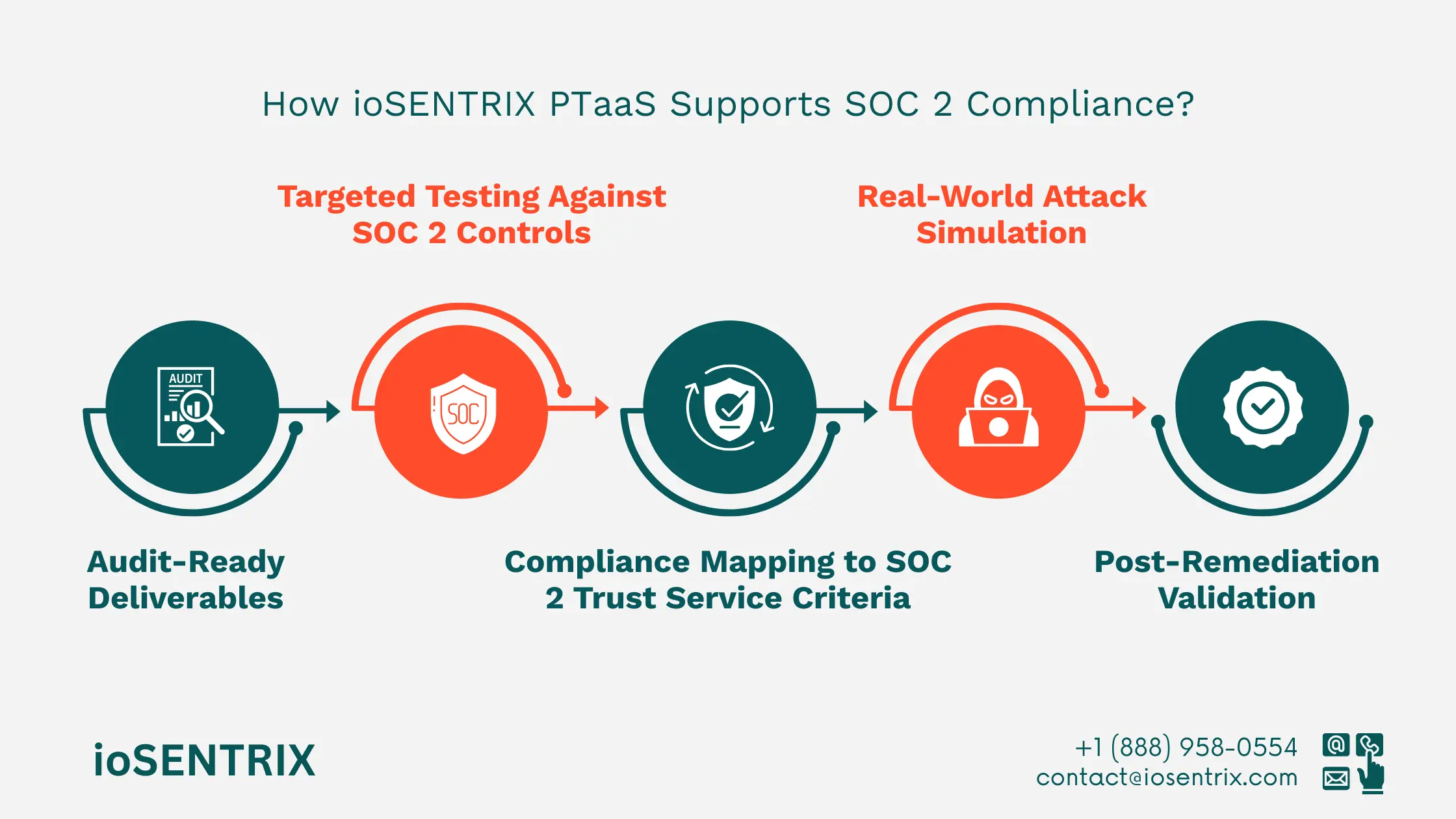
ioSENTRIX has designed its Penetration Test as a Service (PTaaS) to meet the unique demands of SOC 2 audits. The service provides targeted, audit-ready assessments that map directly to SOC 2 control requirements.
Our testing is aligned with specific SOC 2 controls, including:
With ioSENTRIX PTaaS, organizations receive reports that simplify compliance and reduce audit friction. Deliverables include:
These deliverables ensure auditors receive clear and verifiable evidence of security measures, speeding up the compliance process.
Our penetration testing services are structured around the SOC 2 Trust Services Criteria. By aligning directly with Security, Availability, Confidentiality, Processing Integrity, and Privacy, ioSENTRIX ensures your controls are validated against all five principles.
This structured approach strengthens your compliance objectives and provides greater assurance to auditors, customers, and business partners.
SOC 2 penetration testing is most valuable when it goes beyond checklist validation. At ioSENTRIX, our team conducts attack simulations that reflect real-world threats.
These simulations reveal vulnerabilities traditional assessments might overlook, offering a realistic view of your organization’s security posture.
After issues are remediated, ioSENTRIX performs validation testing to confirm that vulnerabilities have been successfully addressed.
This additional step demonstrates continuous improvement and gives auditors proof that controls remain effective after remediation.
Organizations preparing for SOC 2 audits can gain several benefits by choosing ioSENTRIX PTaaS:
Our service integrates seamlessly with leading compliance automation platforms such as Drata, Vanta, Tugboat, and Secureframe.
This integration allows automated evidence collection, real-time monitoring, and faster reporting, reducing the manual burden of compliance preparation.
ioSENTRIX provides standardized and auditor-trusted deliverables that accelerate the audit process. Well-structured reports make it easier to demonstrate compliance while reducing back-and-forth discussions during assessments.
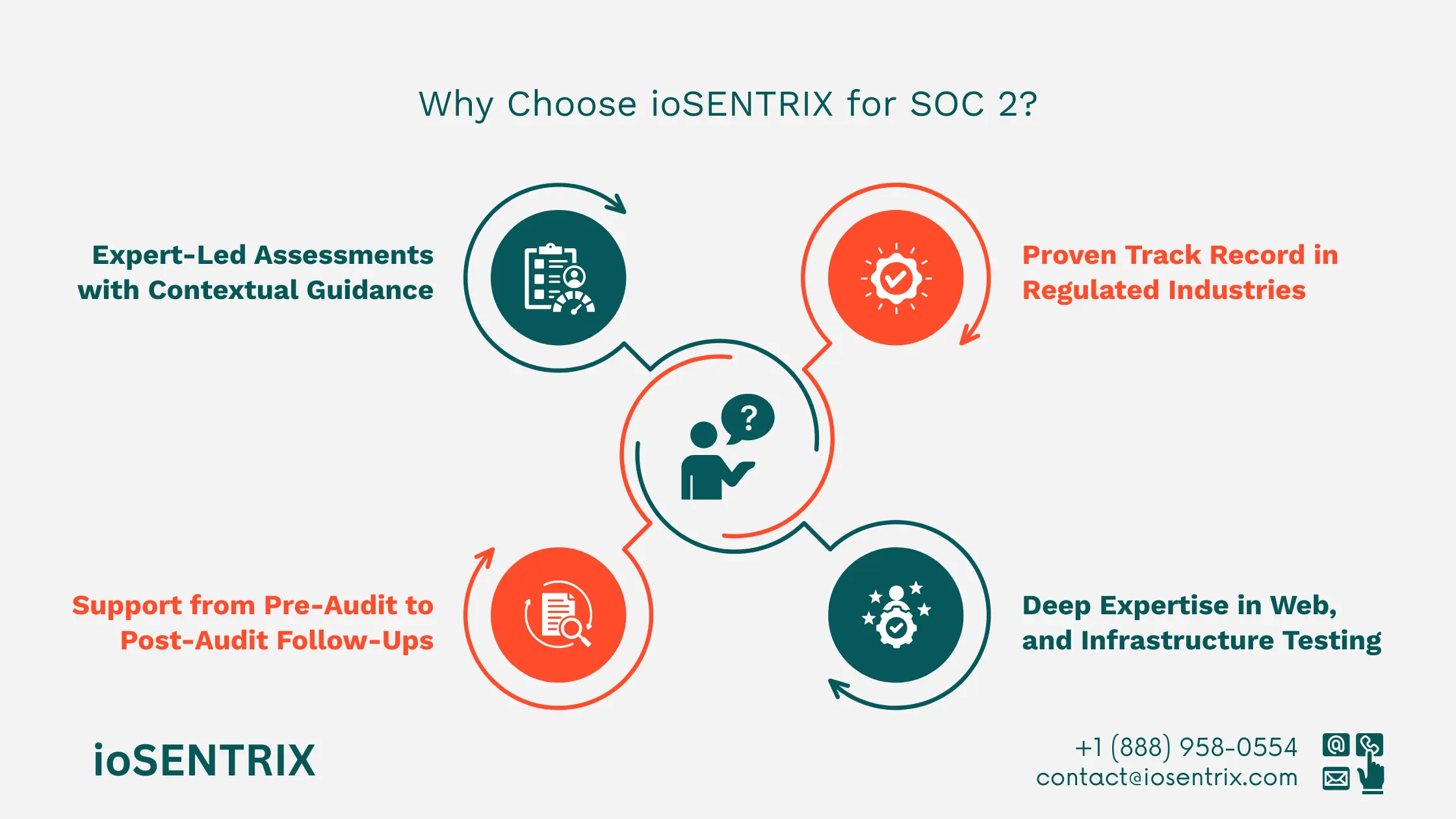
Selecting the right partner for SOC 2 security testing can determine whether your audit experience is smooth or challenging.
ioSENTRIX stands out with its client-focused approach, deep technical expertise, and proven track record.
Our documentation is trusted by auditors, including those from Big 4 accounting firms. ioSENTRIX reports meet rigorous standards and are tailored for enterprise-level assessments.
We understand that audit schedules vary. Our flexible scheduling options allow organizations to plan penetration testing in sync with audit deadlines and evidence submission windows.
ioSENTRIX has successfully delivered penetration testing for companies in SaaS, fintech, and healthcare. Our understanding of industry-specific challenges ensures testing is both relevant and compliant.
Our security team covers every layer of your technology stack. From web applications and APIs to cloud infrastructure and internal networks, we provide end-to-end testing and remediation support.
Unlike automated tools, our penetration tests are led by skilled professionals who provide context-specific recommendations. This ensures your organization receives actionable insights aligned with compliance and business goals.
We support organizations throughout the compliance journey, from pre-audit preparation and assessments to post-audit follow-ups. Our goal is to help you build a long-term culture of security and trust.
While SOC 2 does not explicitly require penetration testing, it is strongly recommended as a best practice to demonstrate control effectiveness.
SOC 2 penetration testing provides proof that your systems are secure and compliant, helping you prevent costly vulnerabilities before they are exploited.
With ioSENTRIX PTaaS, your organization does not just have written policies but verified and tested security controls.
Our expert-led services, detailed reporting, and continuous validation position you for successful audits and long-term resilience against cyber threats.
No, penetration testing is not explicitly required by SOC 2. However, it is highly recommended because it validates the effectiveness of security controls and provides strong evidence for Type II audits.
Most organizations perform penetration testing at least once a year or before major audits. However, more frequent testing may be needed for high-risk industries like fintech or healthcare.
Vulnerability scanning is automated and identifies known issues, while SOC 2 penetration testing involves expert-led simulations of real-world attacks that validate whether vulnerabilities can actually be exploited.
Yes, ioSENTRIX PTaaS integrates with compliance automation tools such as Drata, Vanta, and Secureframe to streamline evidence collection and reporting.
The main benefits include validation of security controls, reduced audit friction, improved risk management, continuous compliance readiness, and stronger customer trust.