The term “Rules of Engagement” might sound intimidating at first, but It’s simply a set of guidelines designed to protect both you as the client and the team performing the testing. The Rules of Engagement, or ROE, clearly outline the details of your penetration testing project.
This includes what will be tested, when the testing will happen, and how it will be carried out. The ROE serves as a clear description of the testing process, making sure everyone involved understands what is happening.
ROE is one of the most important documents in any penetration testing engagement because it prevents misunderstandings, reduces risk, and ensures the project runs smoothly without operational disruptions.
Rules of Engagement (RoE) for penetration testing are predefined guidelines that outline how the test will be conducted. They help align expectations between the organization and the testing team to ensure security, legal compliance, and minimal operational disruption.
Here are the key components of RoE:
A well-defined scope is the foundation of a successful penetration test. It sets the boundaries for what will and will not be tested. This helps minimize risk and maximize the relevance of the findings.
A properly documented scope also ensures compliance with frameworks like SOC 2, ISO 27001, and PCI-DSS, all of which require clear asset definitions before testing can begin.
In-Scope Assets
In-scope assets are the systems, services, and environments explicitly authorized for testing. These assets represent the attack surface that an adversary could realistically target. These typically include:
Modern PTaaS platforms also track in-scope assets continuously, helping organizations keep an up-to-date inventory of what should be tested each cycle.
Out-of-Scope Assets
Out-of-scope assets are systems excluded from the engagement due to potential operational impact, legal limitations, or lack of ownership. These may include:
A clear out-of-scope list also protects organizations from accidental violations of cloud provider policies, which could otherwise trigger automated security responses.
The Timeframe defines exactly when the penetration testing activities will occur. A clear timeline ensures transparency, coordination with internal teams, and minimal disruption to business operations, especially in production environments.
Every penetration test must operate within an explicitly agreed-upon start and end date. This scheduled window allows all stakeholders to align internal monitoring teams, and ensure key personnel are available if any issues arise.
ioSENTRIX works closely with clients to:
Penetration testing may generate alerts or affect system performance, so it’s essential to specify when testing can occur:
Setting a precise timeframe also helps SOC teams differentiate legitimate penetration testing activity from real attacks, reducing false positives.
The Testing Methodology defines the depth and style of testing, as well as the tools and tactics that will (or will not) be used. This ensures all activities remain aligned with the organization’s risk tolerance, compliance obligations, and operational constraints.
The RoE clearly states the type of penetration test to be conducted based on the client's objectives and available information:
Many organizations now prefer methodology alignment with industry standards like OWASP, NIST 800-115, and OSSTMM to ensure consistent testing quality.
It defines how potential risks are identified, mitigated, and controlled during the penetration testing process. Penetration testing often involves interaction with live systems and real data. The RoE must clearly outline how to handle sensitive or production data to prevent accidental exposure or legal violations.
ioSENTRIX follows strict guidelines to ensure:
Read more on: What is Risk Mitigation? Definition and Strategies for Businesses.
Penetration testing may inadvertently trigger alerts or degrade system performance. The RoE outlines specific impact controls to manage and contain these risks:
Documenting a risk-handling plan in advance is especially important for industries like healthcare and finance, where uptime and data protection are critical compliance requirements.
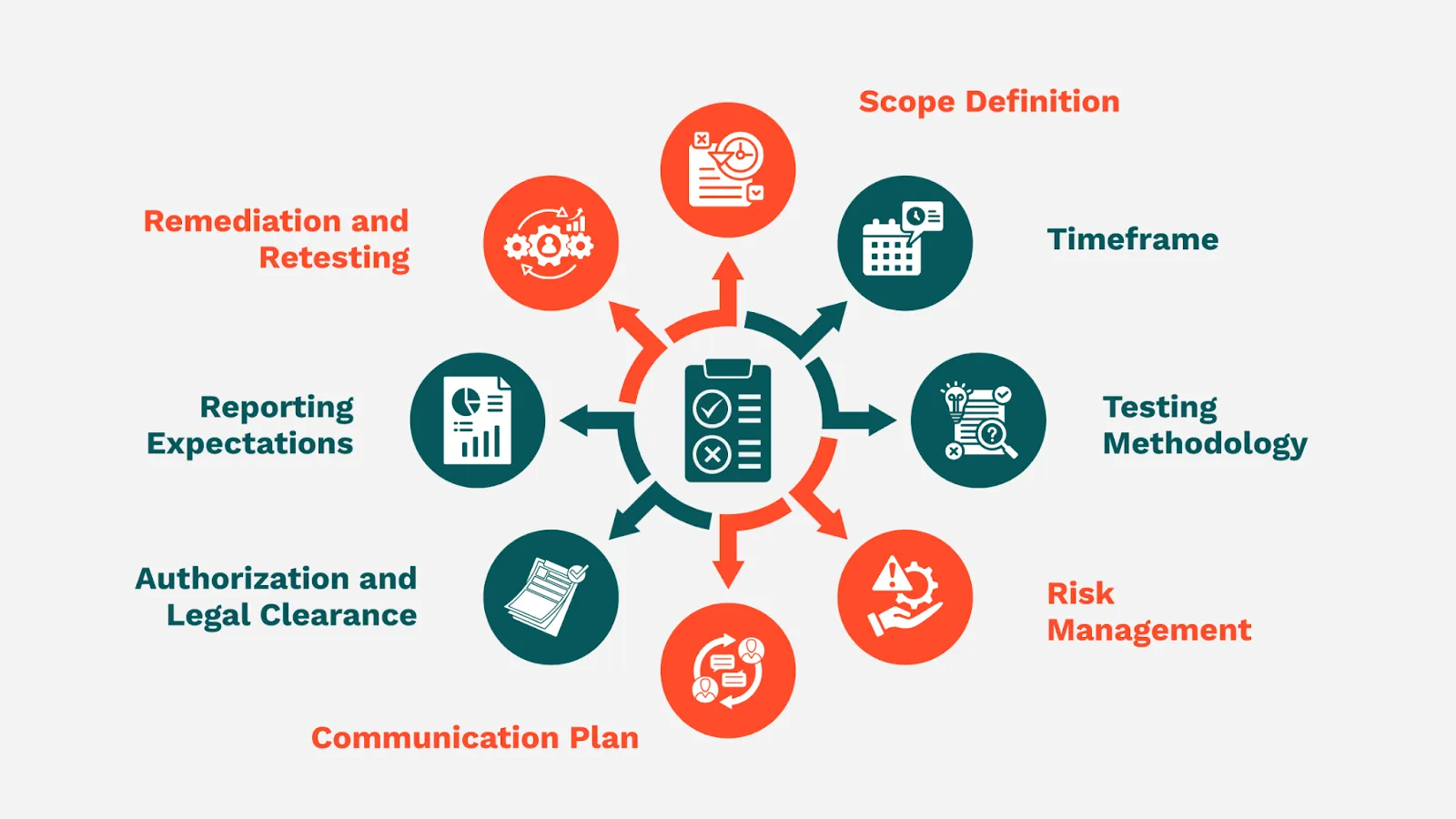
The Communication Plan is a critical component and establishes how information will flow during the penetration test. A solid communication plan prevents miscommunication, reduces downtime, and keeps all stakeholders aligned throughout the engagement.
To streamline coordination, the RoE clearly identifies primary points of contact on both the client and testing team sides. These individuals are responsible for:
Each contact should have defined availability, preferred communication channels (e.g., email, phone, secure chat), and backup contacts in case of unavailability.
The RoE also outlines how and when vulnerabilities or incidents should be reported during the engagement. ioSENTRIX follows a structured, client-approved incident handling process that includes:
The Authorization and Legal Clearance ensures that all penetration testing activities are legally sanctioned and fully documented. This protects both the client and the testing team from legal liability, contractual violations, and misunderstandings with third parties.
Before any testing begins, ioSENTRIX requires formal written authorization from the client. This signed consent form is a legal document that:
Not having proper authorization can expose organizations to legal penalties or violation of service agreements, making this step non-negotiable in every engagement.
Many modern environments rely on third-party platforms or cloud infrastructure (e.g., AWS, Azure, GCP). If these systems are part of the engagement, the RoE must include provisions to:
ioSENTRIX supports clients in managing these third-party notifications and, when needed, can provide templated communications or assist in securing approval.
You may find interesting: What is Cloud Penetration Testing Process?
Reporting explains how the progress will be communicated throughout the engagement and what the client can expect in the final deliverables. This ensures transparency and guarantees the report is structured for both technical and executive audiences.
Depending on the complexity and duration of the engagement, ioSENTRIX may provide daily or weekly status updates. These updates typically include:
Interim updates keep stakeholders in the loop and minimize surprises at the end of the engagement.
The final report is the cornerstone of the penetration testing engagement. It is a professionally structured document that includes:
All reporting is delivered securely and can be customized to align with the client’s internal reporting standards or compliance requirements (e.g., PCI-DSS, ISO 27001, SOC 2). A high-quality report improves cross-department collaboration by giving technical, compliance, and leadership teams a unified view of security posture.
This section outlines what happens after the initial penetration test is completed. This phase ensures that identified vulnerabilities are not only addressed but also validated through follow-up testing.
Once the client has implemented the recommended fixes, ioSENTRIX offers a targeted retesting service to confirm the effectiveness of the remediation efforts. The RoE defines:
Additionally, a Retest Addendum Report is provided, clearly stating which issues were resolved, which remain open, and any new findings introduced during the patching process.
A Rules of Engagement document is created and signed by both parties. It explains what is included in the testing project. Typically, it outlines the areas that will be tested for vulnerabilities, considering how much damage could happen. The testing is also done in coordination with the customer to ensure everything is clear and agreed upon.
Rules of Engagement (ROE) are clear guidelines that show the intent of actions, based on legal, policy, and operational considerations specific to a situation. They are made to ensure that any use of force is carried out in a way that is legally permitted.
The Rules of Engagement (ROE) provide detailed rules and limits for carrying out information security testing. The ROE is set before the testing begins and gives the testing team permission to perform specific activities without needing to ask for further approval.