
Businesses are rapidly moving from traditional on-premise setups to hybrid cloud environments, driven by a wide range of compelling advantages.
Beyond clear cost efficiency and unified data access, organizations are also drawn by the scalability, flexibility, and enhanced collaboration that hybrid cloud solutions provide.
Cloud platforms like Azure Sentinel deliver built-in security safeguards and advanced monitoring capabilities, enabling businesses to detect and respond to threats more quickly than ever before.
Still, making a secure transition to the cloud requires thorough planning and attention to detail.
This shift brings increased security complexity. While cloud service providers are responsible for protecting the underlying infrastructure, your organization must secure its own data, applications, and configurations within the cloud environment.
Misconfigurations, weak access controls, or insufficient visibility into resources can all create vulnerabilities and increase the risk of breaches. That’s why adopting a tailored, layered security approach is crucial.
Regularly reviewing security policies, implementing identity and access management best practices, and conducting proactive assessments are essential to maintaining a strong security posture as your business evolves.
Cloud penetration testing uses real-world attack simulations to actively assess a company’s cloud security. This process helps security teams identify weaknesses and find vulnerabilities that hackers could exploit.
Traditional penetration testing targets a single, well-defined on-premise network. In contrast, cloud vulnerability testing is more complex. Cloud environments are dynamic and distributed, which blurs the lines between system parts.
This means security analysts need deep knowledge of cloud-native architecture and strong coordination to gather data and uncover threats. We go beyond simple scans to perform detailed cloud vulnerability testing.
Embracing cloud services means entering a partnership where security is a joint mission between you and your provider. While your enterprise or virtual network runs on the provider's robust infrastructure, hidden vulnerabilities can still lurk beneath the surface.
Our services are designed to address critical cloud infrastructure security risks. Cyber adversaries are quick to seize these opportunities, using unnoticed activity within virtual machines to launch their attacks.
Just one overlooked flaw in a shared library can open the door to threats against both your systems and your provider's virtual machines. True protection demands swift, coordinated action from all sides.
Our cloud penetration testing services shine a light on these hidden risks and help you seal the gaps, delivering peace of mind and robust security for your enterprise.
Our methodology provides comprehensive security coverage for your cloud environment during penetration testing by using advanced cloud penetration testing tools.
Our process begins with a comprehensive cloud security assessment to map your environment. We create a full inventory of all cloud resources in your cloud environment.
This ensures we see the entire attack surface and do not overlook components. We use cloud-native and third-party tools to identify compute, storage, network, and IAM entities.
We identify and address misconfigurations. Our team follows the best practices for each major cloud provider, including AWS, GCP, and Azure.
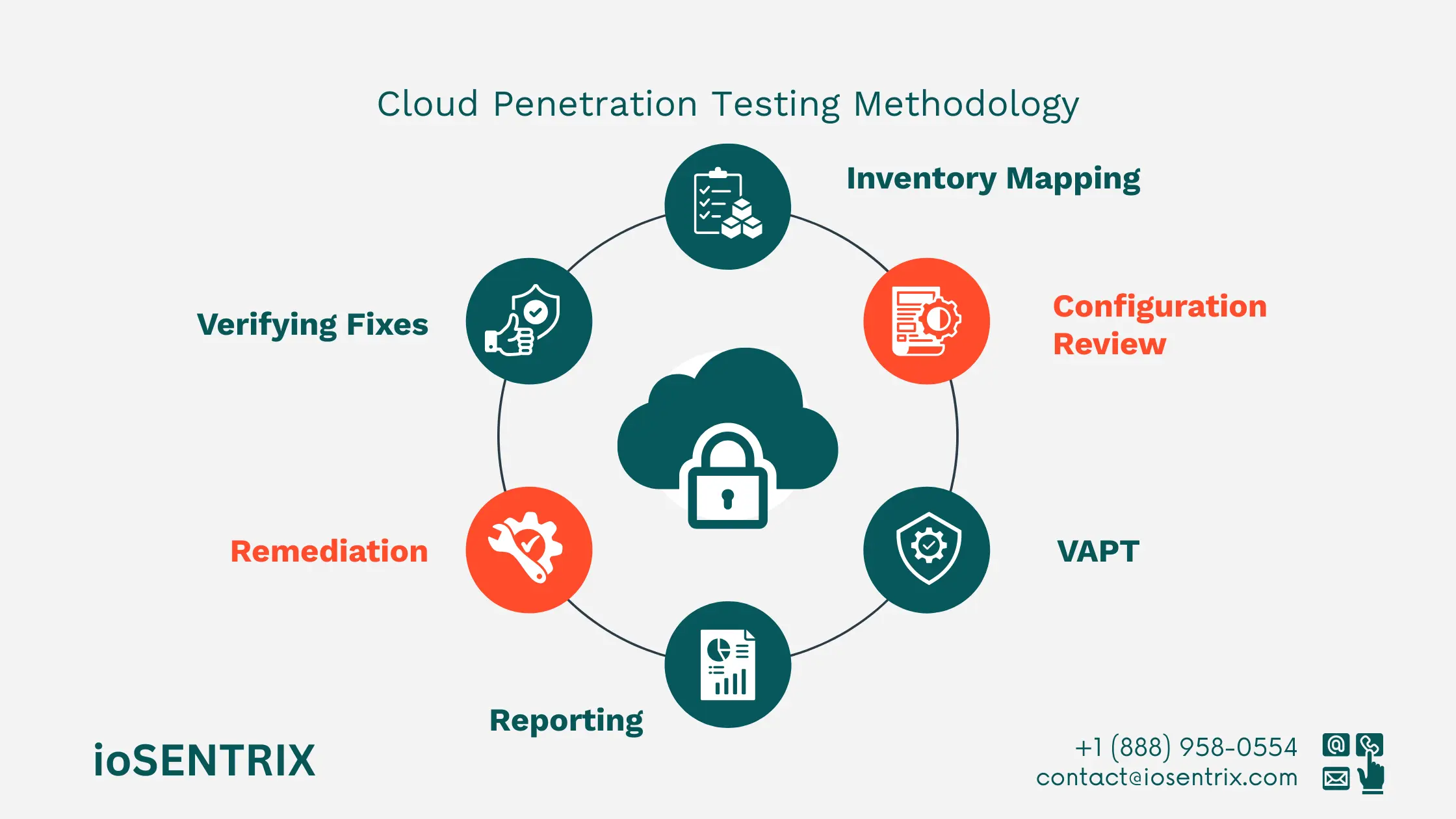
Our approach combines automated scanning and manual testing to identify and exploit vulnerabilities relevant to your cloud environment. Our VAPT process also includes dedicated testing for cloud application security.
We leverage specialized tools, such as AWS Inspector, Azure Security Center, and Google Cloud Security Command Centre, to efficiently detect potential weaknesses.
We deliver clear, concise reports suited to both technical and non-technical stakeholders. Reports include visual aids, clear explanations of each vulnerability, their impact, and reproduction steps.
We use the CVSS system to prioritize findings and provide actionable remediation steps for developers.
We work with your development teams to effectively address the vulnerabilities found during the test.
We retest your environment to confirm all vulnerabilities are fixed, with a focus on critical issues such as IAM permissions.
To ensure a successful and effective cloud security assessment, follow these best practices:
At ioSENTRIX, we go far beyond basic cloud scans. Our expert team uncovers hidden risks and subtle vulnerabilities within your hybrid cloud environments, leveraging years of specialized experience in cloud-native architectures, containers, serverless technologies, and advanced IAM frameworks.
We don’t just identify issues—we provide clear, actionable reports tailored to your environment, ensuring that remediation steps are easy to follow and implement.
Our commitment doesn’t stop at recommendations. We conduct follow-up checks to verify that your security fixes are effective, helping you maintain a robust, resilient security posture over time.
With ioSENTRIX, your cloud security program is not only compliant with industry standards but also proactive, adaptive, and prepared to address emerging threats.
Reach out to us today to request a customized cloud security assessment designed to address your organization’s unique needs and challenges.
It is a controlled test where ethical hackers find weaknesses in your cloud environment so they can be fixed before cybercriminals exploit them.
Our expert team is ready to partner with you, providing guidance and support to help strengthen your defenses, reduce risk, and ensure ongoing protection. Contact us today to request a tailored cloud security assessment that aligns with your organization’s unique needs and objectives.
Both find security weaknesses. However, cloud penetration testing specifically focuses on cloud-based systems and services and addresses the unique challenges of the shared responsibility model.
Cloud application security focuses on protecting the applications you deploy in the cloud. This includes everything from the code itself to the APIs, containers, and serverless functions it uses. It ensures your apps are secure from common web vulnerabilities and misconfigurations.
Free tools are a good starting point for basic scans, but they are not sufficient for a comprehensive cloud penetration testing tools assessment. They often miss complex vulnerabilities and can't provide the in-depth analysis and expert validation required to truly secure an enterprise-level environment.
An ioSENTRIX cloud environment penetration test is a hands-on, expert-driven simulation of a real attack. We don't just provide a report; we give you a roadmap for remediation and a clear understanding of your true security risk. We test for vulnerabilities that automated tools can't find.
The most significant threats to cloud infrastructure security are misconfigurations, weak access controls (IAM), and unpatched software. These issues create exploitable entry points for attackers, making them a primary target for malicious activity.
A vulnerability scan is an automated process that identifies known weaknesses. Cloud vulnerability testing goes a step further by using manual techniques and expertise to validate and exploit those vulnerabilities in a controlled environment, revealing their real-world impact on your systems.
A cloud security assessment is a comprehensive review of your entire cloud environment. It evaluates your security policies, configuration, access controls, and incident response readiness to identify weaknesses and ensure compliance with industry best practices.