
The intersection between gaming and cybersecurity has never been more critical. What was once considered a niche concern is now a top priority for developers, console manufacturers, and publishers alike.
Today, gaming platforms are no longer just entertainment systems—they are fully connected, intelligent ecosystems that integrate cloud services, online multiplayer, social interaction, and real-time transactions.
With this increased connectivity comes greater complexity and a broader attack surface. Modern gaming hardware—including consoles, handhelds, VR/AR devices, and IoT-based gaming peripherals—are built on advanced software stacks and embedded systems. These devices communicate constantly with external networks and applications, which makes them attractive targets for hackers and modders.
So, the penetration testing of gaming hardware consoles is no longer optional—it’s essential. Pentesting helps uncover vulnerabilities that could compromise system integrity, expose intellectual property, or enable cheating and piracy.
The potential for exploitation in gaming hardware grows exponentially. Unlike traditional software applications, gaming consoles and devices combine both hardware and software vulnerabilities. This creates unique and often overlooked risks.
There have been multiple instances where major consoles have been exploited—whether through firmware vulnerabilities, side-loading of unsigned code, or even chip-level attacks. These breaches often result in:
Modern consoles aren’t just gaming devices—they’re multifunctional, internet-connected platforms. They support everything from game downloads and in-game purchases to voice chat and social features. This creates numerous entry points for attackers, including:
Each of these components can be a vector for compromise if not properly secured.
Hackers often target firmware to gain persistent, low-level access to the system. Firmware vulnerabilities can allow attackers to escape security restrictions, load unauthorized software, or permanently alter system behavior. Similarly, unsecured bootloaders can be exploited to jailbreak consoles and open the door to piracy and cheating.
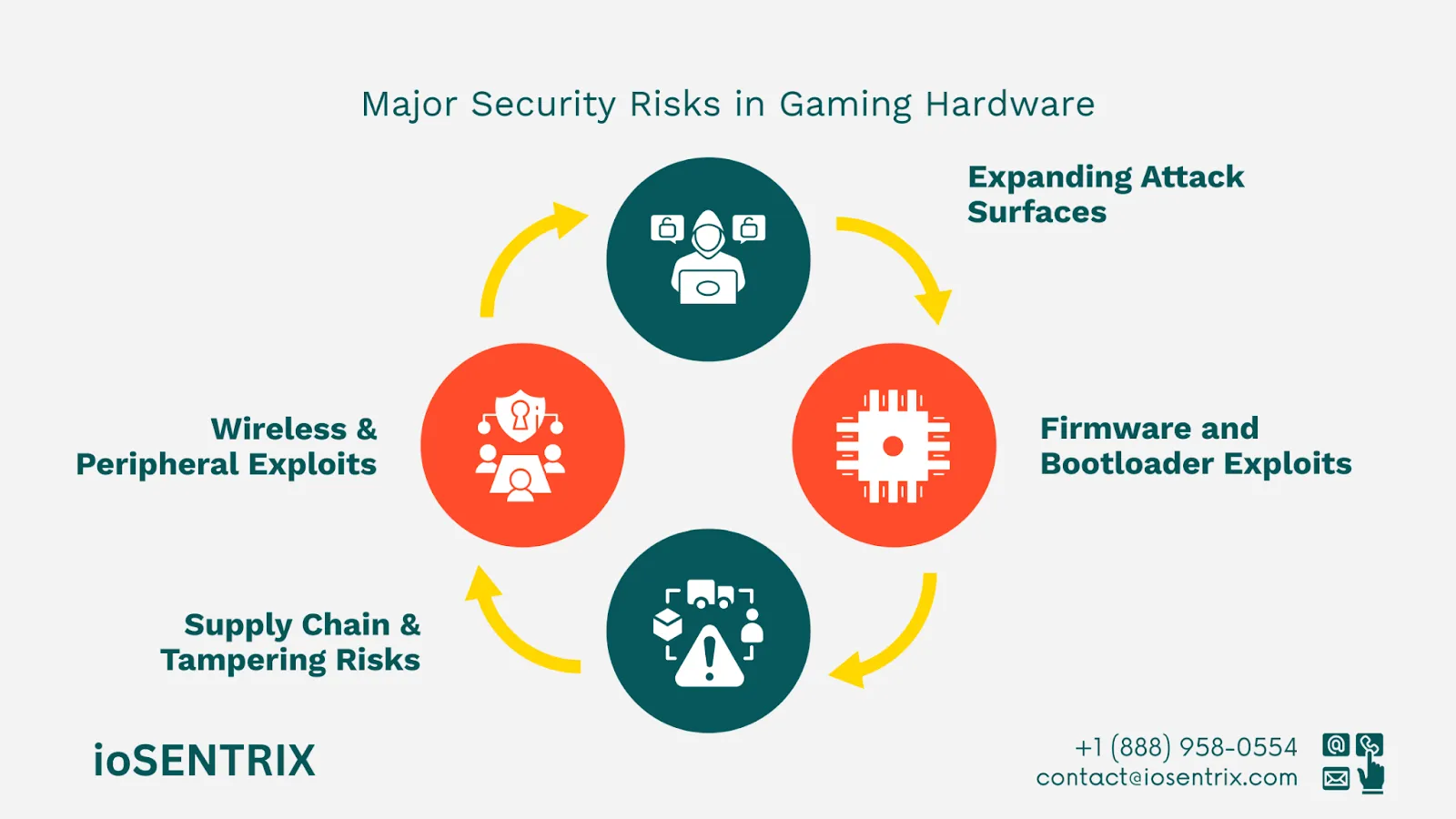
Gaming hardware may pass through multiple vendors and manufacturers before reaching end users. Any of these touchpoints, particularly in an outsourced environment, can introduce supply chain risks, including the insertion of malicious components or pre-loaded malware.
Many gaming devices rely heavily on Bluetooth and Wi-Fi to connect controllers, headsets, and online services. If these interfaces are not properly secured, attackers can inject malicious commands, intercept data, or spoof devices. Additionally, USB ports and memory cards present physical access risks if not hardened against rogue devices.
Penetration testing for gaming hardware consoles simulates real-world attacks on physical gaming devices to identify and exploit vulnerabilities before threat actors can. It delves deeper into the physical and embedded systems of a device, and requires a blend of cybersecurity expertise, hardware engineering knowledge, and reverse engineering techniques.
Gaming consoles are complex, purpose-built systems with proprietary hardware, tightly controlled operating environments, and integrated peripherals. Pentesting these systems requires testers to:
The consequences of a successful hardware exploit can be severe. Attackers could:
Hardware pentesting helps identify and fix these issues proactively—before the console hits the market or a new firmware version is released.
For game studios and hardware manufacturers, integrating pentesting into the development lifecycle ensures:
The gaming industry is no longer just about entertainment—it is a high-value, high-visibility sector that operates in a constantly connected digital ecosystem. With millions of users, in-game economies, competitive esports, and IP-driven business models, gaming platforms have become attractive targets for cyberattacks.
For game developers and hardware manufacturers, the security of gaming consoles is essential not just for user safety, but for maintaining brand reputation and long-term business viability.
One of the most compelling reasons to invest in hardware pentesting is to protect against piracy and revenue loss. Hardware vulnerabilities that allow users to jailbreak consoles or bypass digital rights management (DRM) systems can lead to unauthorized distribution of games and premium content.

In online and competitive gaming environments, fairness is everything. If a console is compromised and used to run modified firmware or cheat tools, the integrity of the game—and the user experience—is immediately at risk.
Unchecked cheating damages player trust, deters new users, and can result in community backlash. Hardware pentesting ensures that:
Modern gaming consoles collect and process a wide range of sensitive information. If a hardware flaw allows unauthorized access to this data, the consequences can be severe—including regulatory penalties under data privacy laws like GDPR or CCPA.
Hardware pentesting helps ensure that user data is securely stored, encrypted, and inaccessible to unauthorized processes, thus supporting broader compliance efforts and user privacy expectations.
Brand loyalty in the gaming industry is fragile. A single major security incident involving a console exploit or user data breach can erode consumer trust for years. Gamers expect platforms to be not only engaging but also safe.
Security cannot be an afterthought. It must be integrated into the product development lifecycle from the earliest design stages. Hardware pentesting enables companies to validate assumptions, uncover architectural weaknesses, and build more secure products before they reach the consumer market.
This not only reduces post-launch costs but also accelerates the ability to innovate without fear of introducing systemic vulnerabilities.
While many cybersecurity providers offer general penetration testing services, few possess the depth of expertise and specialized focus required to effectively assess gaming hardware consoles.
ioSENTRIX’s methodology is built on the foundation of industry-specific knowledge. The team brings an understanding of modern gaming hardware, including custom silicon designs, proprietary operating systems, digital rights management (DRM) mechanisms, and the tightly integrated software stacks that power today’s consoles.
With deep familiarity in how consoles interact with cloud services, companion apps, multiplayer networks, and peripheral devices such as controllers and VR headsets, ioSENTRIX is able to perform assessments that are realistic, thorough, and directly aligned to how threats emerge in live environments.
During a hardware console penetration test, ioSENTRIX focuses on a broad set of technical domains that cover the full spectrum of potential vulnerabilities. This includes evaluating the integrity and security of firmware and bootloaders, which are often prime targets for attackers seeking persistent access or to bypass secure boot chains.
Physical access controls are tested to determine whether unauthorized devices or attackers could compromise a console through exposed interfaces like USB ports or debugging connections. Secure storage and memory protection mechanisms are examined to ensure that sensitive user data, such as saved games or authentication credentials, are adequately encrypted and isolated.
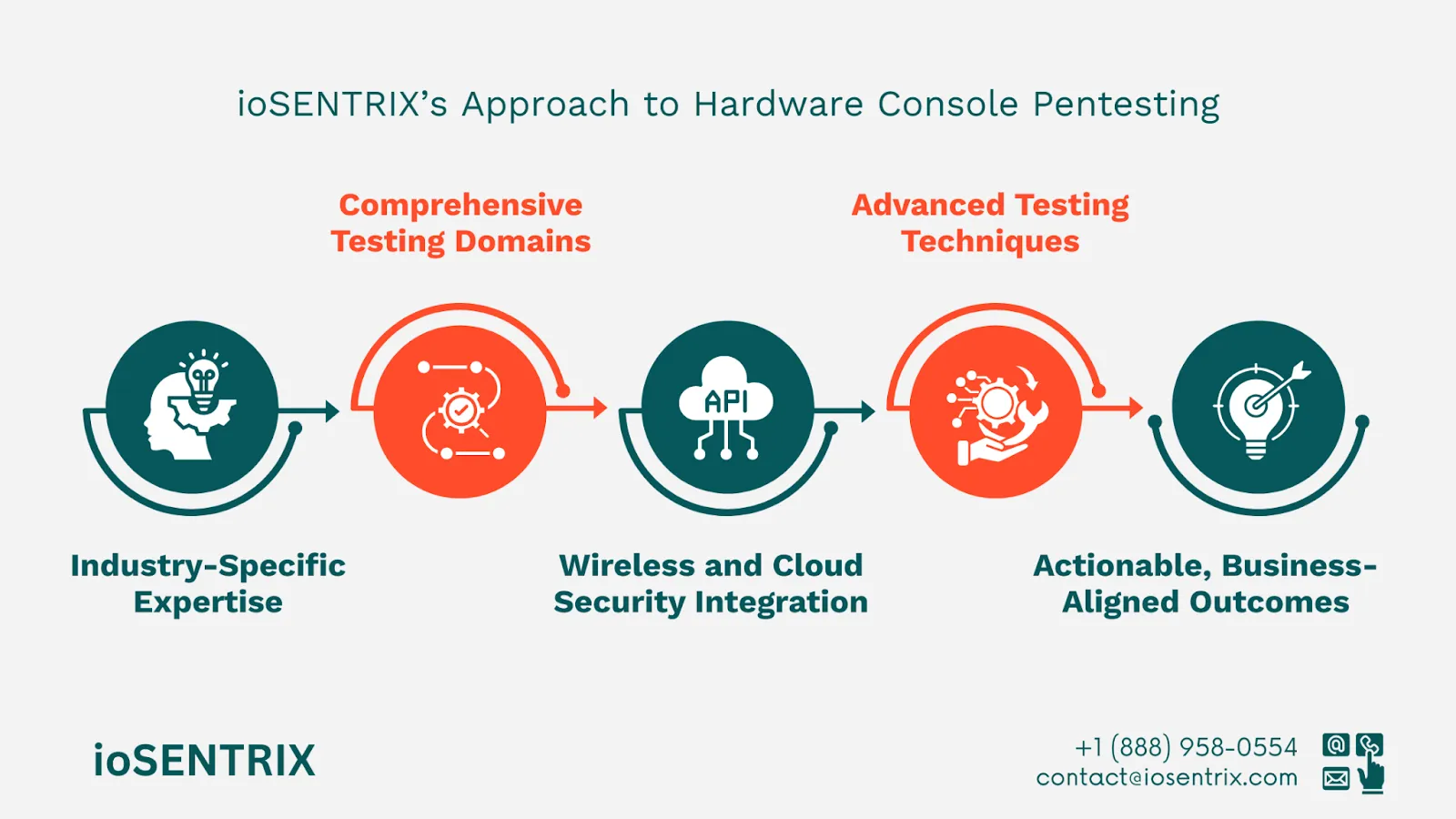
Wireless protocols such as Bluetooth and Wi-Fi are another critical focus. As these channels are essential for device pairing, online gameplay, and content downloads, ioSENTRIX ensures they are configured securely and are resistant to spoofing, eavesdropping, and injection attacks.
The firm also assesses:
To simulate the kinds of advanced threats that gaming companies may face, ioSENTRIX employs advanced testing techniques such as hardware fuzzing, side-channel analysis, reverse engineering of firmware binaries, and exploitation of low-level chip interfaces like JTAG or UART.
What truly sets ioSENTRIX apart is not just its technical rigor but also its commitment to deliver actionable, business-aligned results. The findings from each assessment are translated into practical, prioritized recommendations that consider both technical remediation and business impact.
Reports are designed to be accessible to multiple audiences including firmware engineers and development teams, product owners, legal counsel, and executive leadership.
As gaming continues to push technological boundaries, organizations must rethink how they approach cybersecurity leadership. The stakes are no longer limited to data breaches or downtime—they include reputation, revenue, fairness, and user trust.
While traditional vCISOs and generic security services may offer strategic advice or surface-level testing, they often fall short when it comes to deep, technically empowered, and risk-driven engagement—especially in the dynamic and complex world of gaming hardware and software.
ioSENTRIX acts as more than just a vendor—it becomes a strategic partner. From console hardware pentesting to application security, cloud architecture, and anti-cheat defenses, ioSENTRIX delivers integrated, actionable cybersecurity solutions tailored to the unique needs of game developers, publishers, and platform creators.
If you're ready to take a technically advanced approach to secure your gaming ecosystem, we invite you to explore ioSENTRIX’s gaming cybersecurity services or book a consultation with our team.
Contact now to secure the future of play—together.