PTaaS in a DevSecOps workflow is a cloud-based penetration testing model that integrates continuous testing, automation, and human validation directly into CI/CD pipelines.
This model improves security by making testing an ongoing process rather than a one-time annual activity.
PTaaS platforms provide on-demand assessments, real-time visibility, and automatic retesting, ensuring vulnerabilities are detected immediately as code changes occur.
PTaaS delivers structured penetration testing aligned with DevSecOps principles, where security shifts left and becomes part of daily development operations.
Research from Gartner shows that DevSecOps teams adopting continuous testing reduce security incident probability by 30% due to early detection during build stages.
DevSecOps workflow security is the practice of integrating automated and manual security controls into every phase of the CI/CD pipeline.
It ensures that code is tested during development, build, staging, and deployment, not after release. This includes SAST, DAST, IAST, dependency reviews, container scanning, and policy enforcement.
DevSecOps aims to eliminate late-stage vulnerabilities by embedding security checks early. According to a study by IBM, fixing vulnerabilities during build stages reduces remediation costs by up to 85%, proving why DevSecOps security integration is critical.
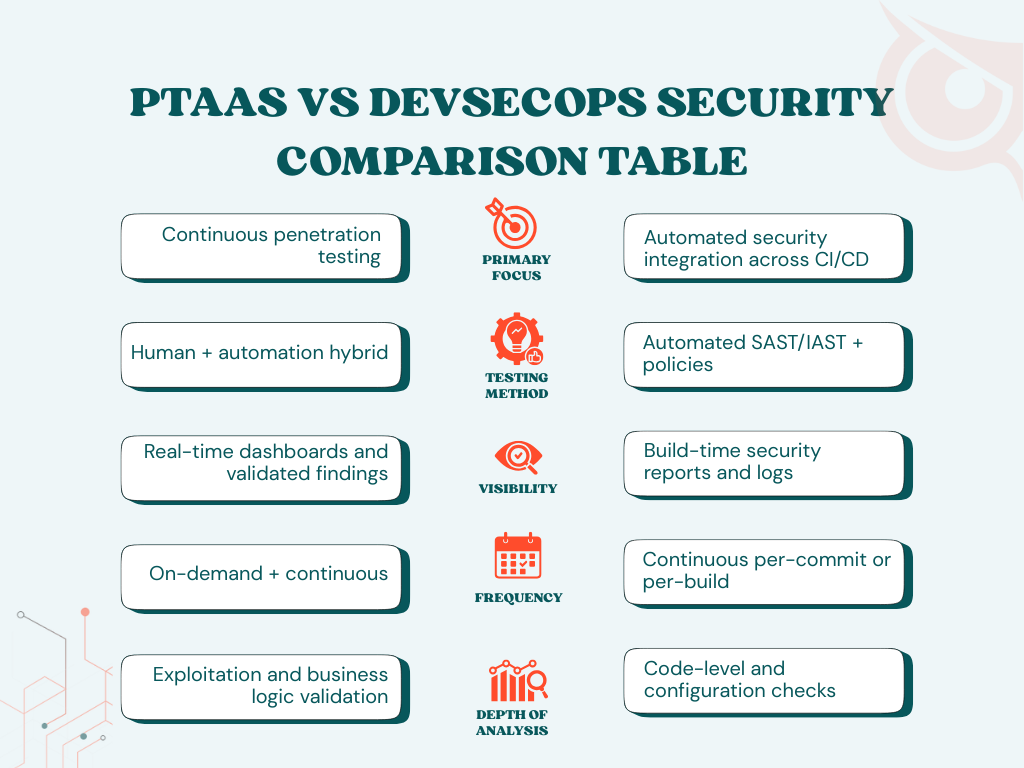
PTaaS focuses on continuous penetration testing, where testers and automation probe applications, APIs, and infrastructure for exploitable vulnerabilities.
DevSecOps workflow security focuses on integrating automated security checks into the development lifecycle.
While both improve security posture, PTaaS brings human-validated exploitation attempts into a DevSecOps pipeline, bridging the gap between automated checks and real attacker behavior.
Integrating PTaaS requires aligning penetration testing processes with automated build and release activities. Below is a complete workflow designed according to your guideline structure.
The first step is connecting repositories and deployment pipelines to the PTaaS platform. The platform ingests application endpoints, environments, and API definitions while mapping assets to release cycles.
This allows PTaaS to automatically trigger a test whenever builds are deployed or major features change.
ioSENTRIX supports CI/CD tools like GitLab, Jenkins, GitHub Actions, and Azure DevOps, enabling tests to run automatically without manual scheduling.
After integration, DevSecOps teams define testing rules such as:
PTaaS platforms classify assets and assign risk scores. ioSENTRIX ensures expert testers validate critical workflows, while automation monitors low-risk or unchanged areas.
This hybrid model reduces false positives and ensures business-logic vulnerabilities are detected.
The system automatically launches pentests whenever a new build reaches staging. This aligns with DevSecOps objectives by ensuring:
This structured integration guarantees every release remains secure without slowing development.
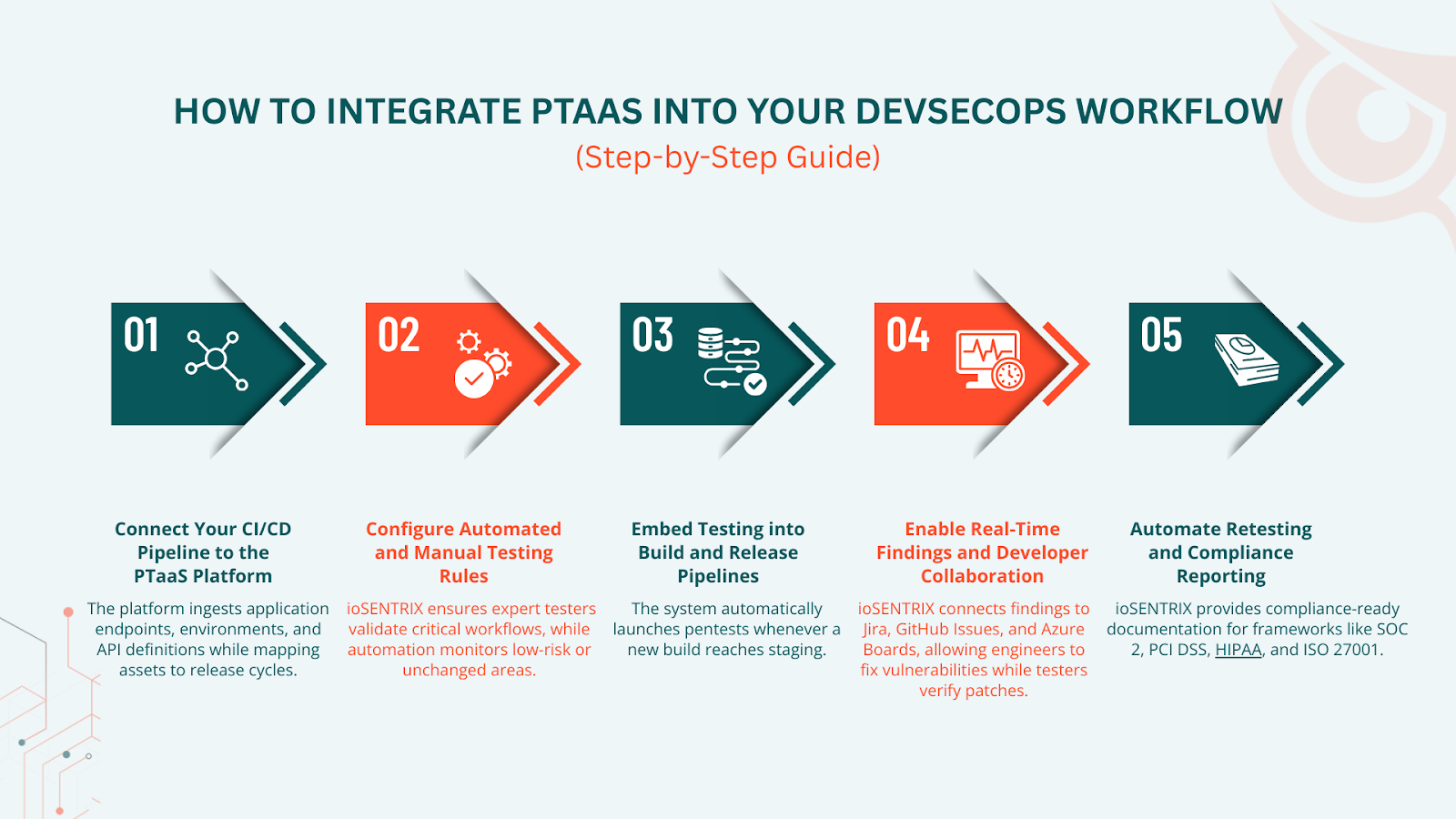
Developers receive instant findings through PTaaS dashboards, CI/CD logs, and ticketing integrations. ioSENTRIX connects findings to Jira, GitHub Issues, and Azure Boards, allowing engineers to fix vulnerabilities while testers verify patches.
This tight feedback loop improves remediation time, which Ponemon Institute reports reduces breach risk significantly when fixed within 48–72 hours.
Retesting becomes automatic after a fix merges, and results sync back into the pipeline. ioSENTRIX provides compliance-ready documentation for frameworks like SOC 2, PCI DSS, HIPAA, and ISO 27001.
This removes manual reporting overhead and ensures DevSecOps teams achieve audit readiness continuously, not once per year.
Choose PTaaS If You Need:
Organizations choose PTaaS when they require real attacker-style validation. PTaaS provides deep exploitation attempts and business-logic testing that automated tools cannot replicate.
This ensures high-risk systems remain secure even during frequent deployments.
Choose DevSecOps Automated Security If You Need:
DevSecOps automation is suitable when teams need scalable, fast, code-driven security checks across numerous services.
Automated testing improves developer velocity but does not simulate complex attacks.
Integrating PTaaS into a DevSecOps workflow transforms security from an annual checkbox activity into a continuous, automated, and expert-validated process.
Businesses that rely solely on automated scans face incomplete coverage, while those limited to annual pentests expose themselves to vulnerabilities throughout the year.
ioSENTRIX bridges this gap by combining real human expertise with automation, ensuring that every release is tested deeply, every vulnerability is validated, and every team remains compliant and secure.
As organizations scale their development speed, hybrid PTaaS becomes the most effective model for maintaining strong security resilience.
DevSecOps integration embeds security tools and processes into every stage of the CI/CD pipeline.
Security integrates by adding automated scans, policies, access controls, and PTaaS validation into each development phase.
Automation, SAST, DAST, dependency analysis, IaC scanning, and continuous pentesting must be integrated across all phases.
Common tools include GitLab, GitHub Advanced Security, Snyk, OWASP ZAP, Burp Suite, and PTaaS platforms like ioSENTRIX.