
Digital payment systems are now a critical backbone of global commerce. However, with this convenience comes increased exposure to an expanding cyber environment. Hackers are constantly targeting vulnerabilities in web applications, mobile platforms, APIs, and network infrastructure to manipulate or steal sensitive payment data.
Secure financial transactions are no longer just a matter of regulatory compliance—these are essential to maintain customer trust, business continuity, and brand integrity. Payment breaches can result in significant financial losses, reputational damage, legal consequences, and long-term customer attrition.
As a result, organizations must take an end-to-end approach to protect the payment ecosystems they depend on.
Digital commerce has introduced remarkable convenience—but it has also exposed organizations to complex cybersecurity threats. As businesses increasingly rely on web applications, mobile apps, APIs, and cloud infrastructure to facilitate payments, attackers have more entry points than ever before to exploit.
Payment systems are prime targets for cybercriminals because of the high-value data they handle—credit card numbers, customer credentials, banking information, and transaction records. Threat actors use techniques to compromise these systems such as man-in-the-middle (MITM) attacks, SQL injection, cross-site scripting (XSS), insecure direct object references (IDOR), and API abuse.
The consequences of these breaches are severe. Beyond direct financial theft, organizations may face steep regulatory fines, legal liabilities, and the loss of consumer trust.
Notable incidents in recent years have demonstrated how a single vulnerability can lead to millions of dollars in damages and years of reputational repair such as:
A misconfigured AWS Web Application Firewall (WAF) allowed a former employee to exploit a server-side request forgery (SSRF) vulnerability. Over 100 million credit applications were exposed, including names, addresses, credit scores, and some Social Security numbers.
Cost: Capital One agreed to pay $190 million in a class-action settlement and an additional $80 million in regulatory fines.
Lesson: A single configuration flaw in a cloud-based application can compromise sensitive financial and personal data at scale.
Attackers exploited a known vulnerability in Apache Struts (CVE-2017-5638) that had not been patched in time.Personal data of 147 million people was exposed, including names, Social Security numbers, and credit card data.
Cost: The total financial fallout exceeded $700 million in settlements and penalties.
Lesson: Delayed patching of application-layer vulnerabilities can lead to catastrophic breaches, particularly in systems holding sensitive financial information.
A malicious script was injected into the airline’s payment page via a third-party service (Magecart attack). Data from over 400,000 payment transactions was compromised.
Cost: Initially fined £183 million (reduced to £20 million) under GDPR for failure to protect customer payment data.
Lesson: Front-end payment interfaces are especially vulnerable to supply chain attacks and client-side injection flaws.
It is no longer sufficient to rely on traditional security measures or periodic audits. Organizations must adopt a continuous testing mindset to address vulnerabilities before adversaries do. This is particularly true for applications and network systems that form the backbone of digital payment infrastructure.
Digital payment systems are built on a tightly integrated foundation of applications, APIs, and network infrastructure. Each component plays a critical role in processing, validating, and securing transactions. If even one of these layers is compromised, the entire system becomes vulnerable to exploitation.
At the application level, vulnerabilities can lead to unauthorized access, data leakage, and fraudulent activity. Common weaknesses such as broken authentication, insecure API endpoints, logic flaws, and poor input validation can allow attackers to manipulate transactions or disrupt services.
On the network side, weaknesses in configuration, segmentation, or access control can provide attackers with a pathway into the organization’s core payment infrastructure. Once inside, they may attempt lateral movement, privilege escalation, or data exfiltration. Misconfigured firewalls, exposed services, or inadequate monitoring can all become conduits for serious breaches.
Regulatory frameworks like PCI DSS, GDPR, and ISO 27001 require organizations to demonstrate due diligence in protecting payment data. Application and network pentesting is a key component of meeting these compliance requirements.
It not only finds critical vulnerabilities but also helps establish defensible security measures in the eyes of regulators, partners, and customers.
Application-layer vulnerabilities are among the most exploited vectors in payment system breaches. ioSENTRIX tackles these threats head-on through its comprehensive application penetration testing services that find hidden weaknesses in the systems that process, store, and transmit payment data.
The ioSENTRIX application pentesting methodology goes beyond automated scans to deliver in-depth, manual assessments of web and mobile applications, payment portals, and APIs. The focus is on replicating real-world attack scenarios to analyse how well applications can withstand skilled adversaries.
Each engagement begins with a deep understanding of the application’s architecture, business logic, and the specific ways it interacts with payment processes. Particular emphasis is placed on critical areas such as authentication and session management.
Input validation and injection testing are conducted to detect vulnerabilities like SQL injection or cross-site scripting that could allow unauthorized manipulation of payment data.
ioSENTRIX also scans payment workflows to identify logic flaws, such as the ability to alter transaction amounts, circumvent payment validation, or interfere with the checkout process.
APIs are tested for proper authentication, rate-limiting, encryption, and data handling practices. The goal is to ensure that no sensitive information can be intercepted or manipulated in transit.
What sets ioSENTRIX apart is its focus on actionable outcomes. Every finding is contextualized based on the potential business impact, providing development teams with clear, prioritized recommendations.
While applications often draw the spotlight in payment security, the underlying network infrastructure is just as critical. Payment data travels across a complex web of routers, firewalls, servers, and third-party integrations. A single misconfiguration or exposed service within this network can serve as an open invitation to cybercriminals.
ioSENTRIX addresses this risk through comprehensive network penetration testing, targeting both internal and external environments to find vulnerabilities that could compromise payment infrastructure.
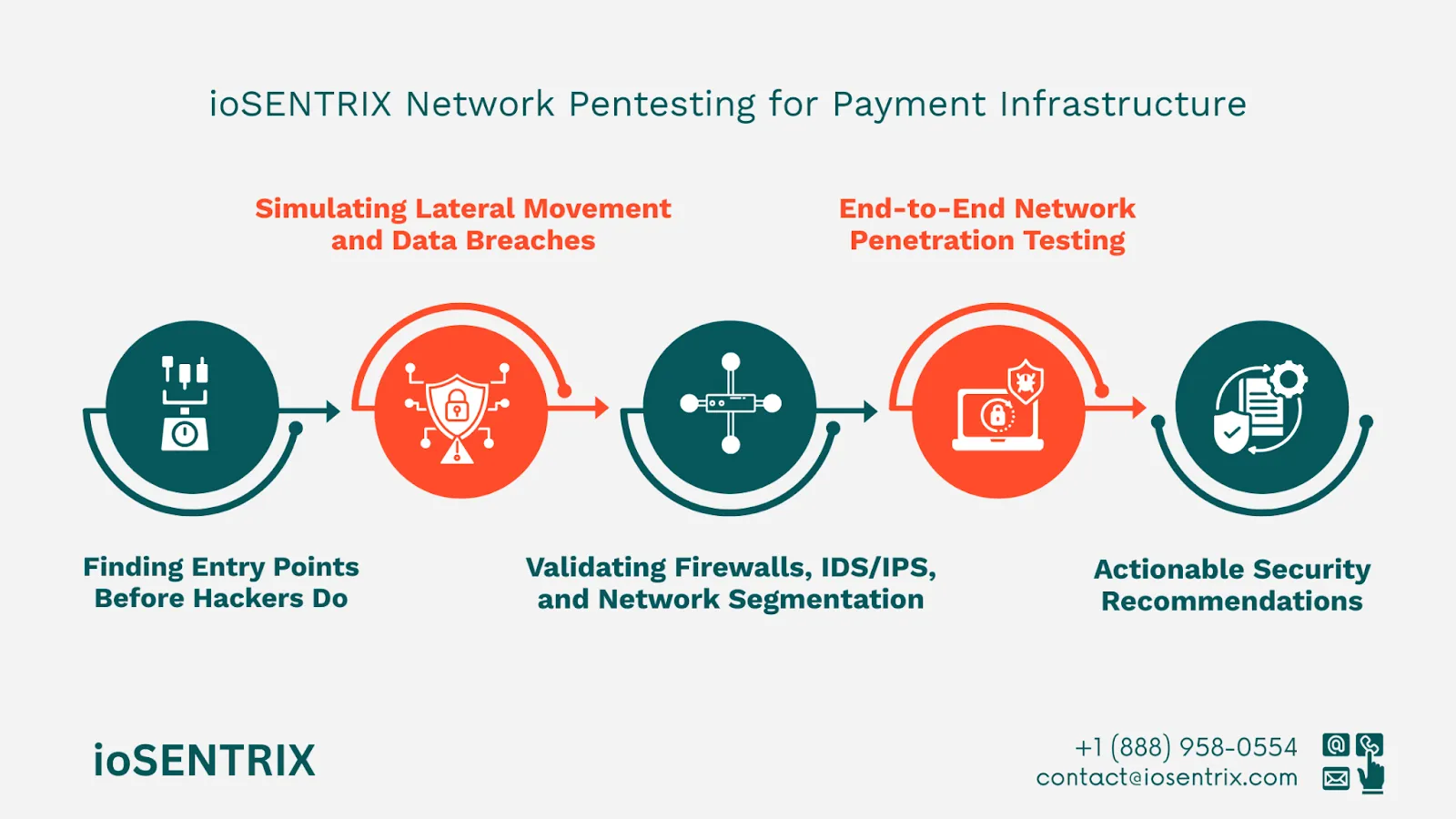
The network pentesting process begins with reconnaissance and threat modeling to understand the organization’s architecture, asset exposure, and trust boundaries. From there, ioSENTRIX tests external-facing systems to identify insecure ports, outdated services, weak encryption protocols, and unpatched vulnerabilities that may be exploited by attackers.
For internal networks, the focus shifts to identifying paths for lateral movement, privilege escalation, and data exfiltration, simulating what an attacker could do once inside the perimeter.
Special attention is given to firewalls, intrusion detection/prevention systems (IDS/IPS), and network segmentation controls. These systems are tested to ensure that they effectively isolate payment processing environments and block unauthorized access attempts.
Each finding is accompanied by actionable recommendations that align with the organization’s infrastructure and compliance goals. The result is not just a vulnerability report—but a strategic blueprint for hardening your network against real-world attacks.
Cybersecurity is not only a business imperative but also a legal obligation. Regulatory frameworks such as PCI DSS, ISO 27001, SOC 2, and GDPR mandate strict controls over how payment data is processed, stored, and transmitted.
Through detailed testing methodologies, ioSENTRIX helps organizations meet and exceed industry standards. For example, its assessments address PCI DSS requirements around secure application development, access controls, encryption, vulnerability management, and system monitoring.
The network penetration testing element specifically corresponds to PCI DSS requirements for detecting and addressing vulnerabilities within cardholder data environments (CDEs). It also involves verifying the accuracy of firewall configurations and ensuring proper segmentation to separate critical systems from other network segments.
ioSENTRIX bridges the gap between technical findings and compliance documentation. The reports provided are structured to support audit readiness. This not only reduces the burden on internal teams but also improves the organization’s posture during external assessments.
Beyond PCI DSS, ioSENTRIX’s testing also supports broader frameworks such as ISO 27001 and SOC 2 by addressing key control areas like risk assessment, incident response readiness, secure software development, and access governance.
Security testing only delivers true value when its results are both actionable and aligned with business priorities. ioSENTRIX understands that organizations don’t just need technical vulnerability reports, they need clear, context-driven insights that help them make informed decisions in a meaningful way.
Each application and network pentesting engagement at ioSENTRIX culminates in a comprehensive, prioritized report that maps findings to real-world business impact. Vulnerabilities are not only rated by severity, but also by how they could affect specific payment workflows, customer trust, compliance obligations, and operational continuity.
The remediation guidance provided is detailed, practical, and aligned with industry best practices. ioSENTRIX works collaboratively with internal teams to help them understand the root causes of vulnerabilities and implement sustainable fixes. When needed, follow-up support and retesting services are offered to validate that corrective actions have been successfully applied.
As the digital economy grows, so does the complexity and criticality of securing payment systems. Applications, APIs, and networks are no longer isolated components; they form a tightly interconnected ecosystem that must be safeguarded against cyber threats.
ioSENTRIX rises to this challenge by delivering advanced application and network penetration testing services that go far beyond vulnerability detection. Through deep technical expertise, business-aligned reporting, and remediation support, ioSENTRIX helps organizations strengthen their payment infrastructure, meet regulatory requirements, and build trust with their customers.
Explore ioSENTRIX’s pentesting services or connect with our experts to learn how we can help protect your payment systems from end to end.