
Continuous Threat Exposure Management (CTEM) is a program that security professionals can implement to automatically monitor attack surfaces on an ongoing basis.
With more IT and security systems, CTEM helps keep track of potential risks continuously, making it a cornerstone of cybersecurity exposure management.
Identity and access management (IAM) features are an important part of a CTEM program because they ensure that many users and devices are correctly verified when accessing a company’s network. This helps prevent security threats before they happen.
According to Gartner® research, Continuous Exposure Management programs are becoming more popular recently due to:
The research also explains that concerns about exposure issues have moved beyond just fixing software vulnerabilities in commercial products.
Security teams find it overwhelming to handle the increased technology risks on such a large scale.
For organizations like healthcare providers, this means there could be more access points or weaknesses that threat actors can target and take advantage of.
Continuous Threat Management starts with defining the scope, which involves identifying important assets and making sure security goals match the business’s objectives.
This helps ensure resources are used wisely to protect what is most important. For example, a tech startup might focus on securing customer data, intellectual property, and unique algorithms to make smart and effective security investments.
Important factors to consider are:
After defining the scope, the next step is to find vulnerabilities in networks, applications, cloud systems, and IoT devices. This can be done using automated scanning tools and manual checks.
Automated tools quickly identify common issues, while manual reviews help find problems that machines might miss. It is also important to identify all digital assets, including unmanaged and shadow IT systems, to uncover any hidden security gaps.
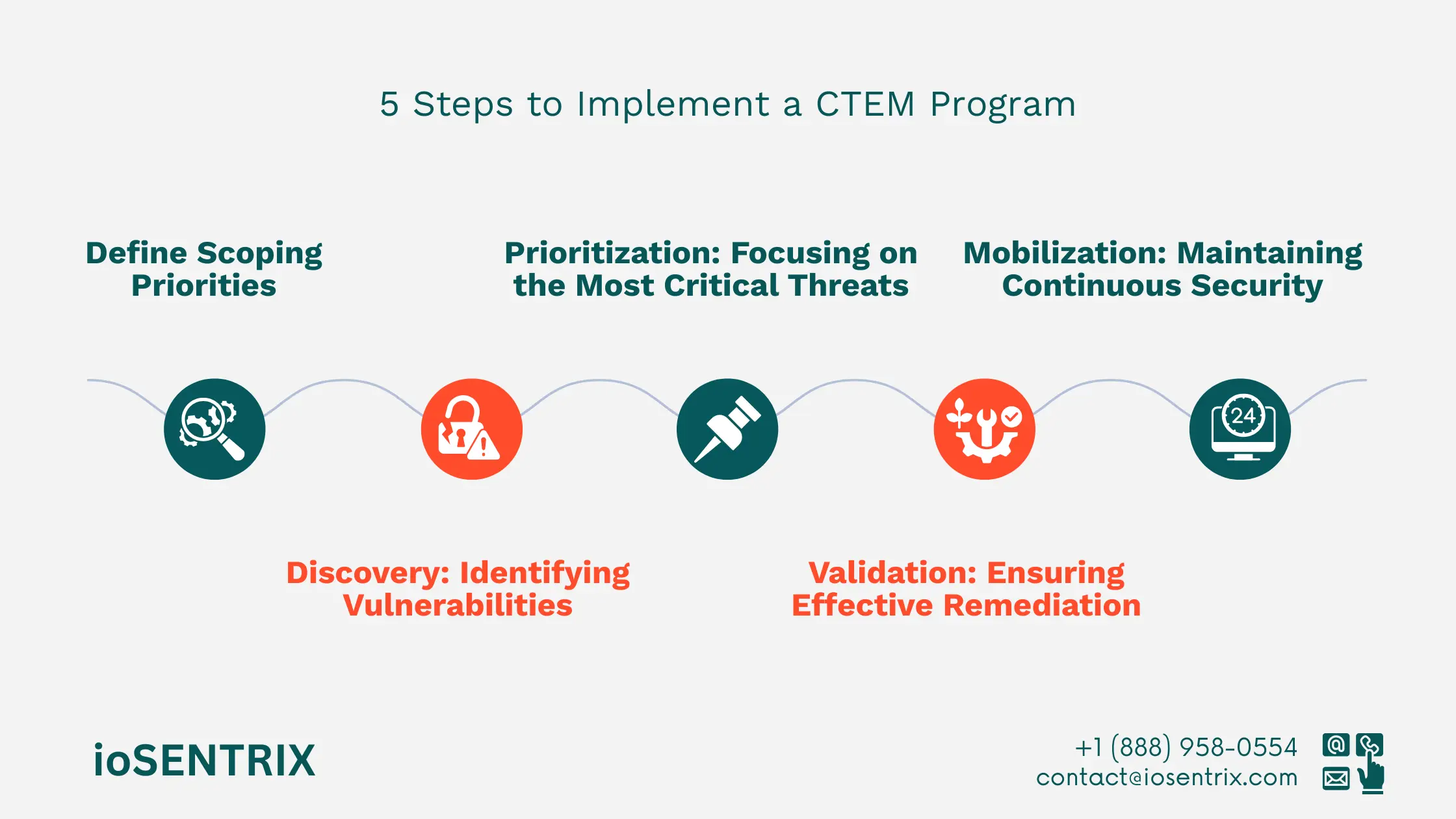
Not all vulnerabilities have the same level of danger. It is important to prioritize them so that security teams focus on the most serious threats first.
Monitoring metrics such as Mean Time to Resolve (MTTR) helps measure how fast critical vulnerabilities are fixed.
Using threat intelligence also helps teams understand attacker methods, so they can better prioritize issues and improve their response strategies.
After fixing vulnerabilities, it is important to verify that the solutions work and have not created new security problems.
This can be done using penetration testing tools or manual red team exercises that imitate real attacks to test the defenses. Validation should also include reviewing system settings to make sure no new risks are introduced.
Without proper validation, security gaps may remain unnoticed, which gives a false sense of safety. To be sure that their defenses are working well, organizations need to carefully check and confirm that their fixes have been successful.
Cybersecurity is a continuous effort. Staying prepared means that Threat Exposure Management stays active and adapts to new threats. This involves regularly updating security procedures, tools, and training.
Regular threat simulations and tabletop exercises are useful for testing and improving incident response plans. Because threats are always changing, fixed defenses are not enough. An ongoing, continuous threat management approach is necessary to stay ahead of attackers.
Organizations use Continuous Threat Exposure Management (CTEM) to avoid frustration. A full system scan often reveals more issues than they can fix.
These issues may come from on-premise, cloud, or containers, and include vulnerabilities, misconfigurations, or identity risks.
Without a way to combine these exposures and understand their real risk, organizations struggle to decide what to fix first.
Traditional tools like vulnerability management or breach and attack simulation (BAS) cannot provide full protection. This is why cybersecurity exposure management through CTEM has become a top priority.
Any organization with a formal cybersecurity program can gain advantages from using Continuous Threat Exposure Management (CTEM), and more organizations are starting to adopt it.
A recent Gartner study of 247 organizations showed that 29% had already put a CTEM program in place. Additionally, 46% were working on developing one.
This means that overall, 75% of these organizations are either using or planning to use continuous exposure management.
XM Cyber observes that many different types of organizations are using our solution to support their threat exposure management programs. For example:
Risk-based Vulnerability Management (RBVM) is a cybersecurity approach that helps organizations reduce risk by focusing on fixing the most important vulnerabilities first.
To do this, organizations use tools to evaluate their current cybersecurity weaknesses and decide how much danger each one presents to their most important assets.
This assessment is based on whether the vulnerabilities are actively being exploited in real-world situations.
Automating this process is very important because of the large number of vulnerabilities, which is why automation tools have been used for many years.
In 2020, there were 17,000 new vulnerabilities reported, which is about one new vulnerability every six minutes. Since attackers quickly develop ways to exploit these vulnerabilities, defenders also need to respond quickly and efficiently.
However, defenders using these tools often find it difficult to manage all cyber vulnerabilities. Even big, well-funded organizations cannot fix every vulnerability they find. There are too many vulnerabilities, and some systems cannot be patched, plus there are dependencies in the supply chain.
It is also important to note that RBVM focuses only on prioritizing vulnerabilities (CVEs). It does not deal with issues related to identity or misconfigurations, which attackers often take advantage of.
Continuous Threat Exposure Management (CTEM) helps to focus and reduce the work needed for fixing issues by prioritizing efforts based on the actual risk to important assets.
It considers all types of exposure, not just CVEs, and looks at how serious the threat really is. It also offers a complete process for cybersecurity exposure management over time.
In this way, continuous threat management improves RBVM by adding more coverage of exposure types, real attacker information, and advice on how to fix problems.
Continuous Threat Exposure Management (CTEM) programs go beyond traditional cybersecurity assessments. It uses cybersecurity tools to match the scope of exposure checks with specific business projects and key threat areas.
It also verifies the company's exposure and fixing priorities by considering the attacker’s point of view and testing how well security controls and incident response plans work.
This helps ensure that security efforts focus on the most important areas for the organization, making security measures more effective and efficient.
Additionally, CTEM offers a full view of risk that can be monitored over time, showing how fixing issues improves overall security.
A CTEM program typically integrates existing parts of a security program to strengthen and automate security efforts in one place.
When it comes to an organization’s attack surface, there are always new threats appearing and new exposures that were not considered risky before.
With many providers available, it can be hard to determine which vendor’s solution is the best fit for an organization. It can also be unclear what is involved in setting up the program.
Let’s explore the different features that a continuous exposure management program might combine to help improve cyber resilience.
Gaps or weaknesses in an organization’s attack surface can quickly become entry points for external attackers, leading to serious damage.
Adding external attack surface management (EASM) features to a CTEM program can strengthen defenses beyond the internal network.
This helps teams identify and fix issues such as exposed passwords, cloud setup errors, and problems with external vendors or services.
.webp)
A CTEM program combines various tools to help protect an organization's attack surface by constantly checking for and finding potential exposures.
It's important to remember the main goal of threat exposure management because it has an important role and involves many different stakeholders' views.
Therefore, it is important to agree on the goals and clear objectives for continuous threat management. This helps security teams focus on what matters most and manage the many alerts from different CTEM tools.
Automating the process of prioritizing these alerts is only possible when the system is set up correctly based on those agreed-upon goals.
If CTEM detects vulnerabilities and assists teams in fixing them, adding digital risk protection (DRP) features can provide a broader view of the chances that network systems have weaknesses. This helps teams understand and address these issues more effectively.
For example, the risk level for a modern, internet-facing application connected to many internal systems could be much higher than an old company webpage that hasn't been visited much in years.
The application with the higher risk level might not currently have any serious vulnerabilities, but it is updated more often than the old webpage.
Since it receives more updates, there is a greater chance of accidental exposures, which increases its overall risk.
Implementing Continuous Threat Exposure Management (CTEM) needs the right tools to support its ongoing and strategic method.
ioSENTRIX helps organizations use CTEM effectively. We offer real-time assessments of vulnerabilities, prioritizes based on business impact, and predicts future risks.
ioSENTRIX provides security teams with its easy-to-understand visual reports and automated insights to reduce exposures and improve their overall cybersecurity exposure management.
Connect with our experts to find out more about continuous exposure management tools and how to select the best one for your organization.