
ISO 27001 is a widely recognized standard for managing information security. It outlines the key requirements that an Information Security Management System (ISMS) should fulfill.
This ISO 27001 Certification Guide provides organizations of all sizes and industries with practical steps to set up, implement, maintain, and continuously improve their ISMS.
Being compliant with ISO 27001 compliant with ISO 27001 means that an organization has established a system to manage risks related to the security of its data. It also means that this system follows all the best practices and principles set out in this international standard.
ISO 27001 encourages a complete approach to information security by examining people, policies, and technology. When an organization follows the ISO 27001 certification process, it helps to manage risks, improve cyber-resilience, and achieve better operational performance.
Unlike a generic ISO 27001 Guide, this article dives deep into the certification journey, the ISO 27001 Certification Process, and how to leverage a Guide to ISO 27001 Certification for long-term success. If you are searching for a practical ISO 27001 Compliance Guide, you are in the right place.
Risk management is usually the most difficult part of implementing ISO 27001, but it is also the most important step in the guide to ISO 27001 certification. It builds a strong foundation for information security in your company.
Risk management includes two main parts:
Risk assessment is the process where a company identifies potential security risks, figures out how likely they are to happen, and considers what the effects might be.
In simple terms, the organization needs to understand all possible problems with their information, how probable they are, and what could happen if they occur.
The goal of risk treatment is to determine which security measures are needed to prevent these potential problems.
The process of choosing these controls is called risk treatment. In ISO 27001, the controls are selected from Annex A, which lists a total of 93 different security controls.
ISO 27001:2022 security controls provide a clear way to handle risks and keep data safe, following international standards. With more than 40,000 organizations around the world using ISO 27001, it plays a key role in improving security practices.
Security controls are a key part of a strong Information Security Management System (ISMS) and help lower the chance of data breaches.
As cybersecurity expert John Smith states:
"ISO 27001:2022 offers a solid framework for managing information security risks."
It is important to understand these controls before putting them into place, so they fit with your organization's goals and legal requirements.
The main parts of ISO 27001:2022 are:
These parts work together to make sure security measures are properly added to your ISMS. This helps better manage risks, meet compliance requirements, and build trust with stakeholders.
Getting ISO 27001 certified is not quick or simple. The time it takes can vary. Getting ISO 27001 certified is not quick or simple. On average, companies should expect to spend about a year on the ISO 27001 certification process.
Below are the main steps outlined in this ISO 27001 compliance guide:
The best starting point is to get familiar with the Standard itself. Having a clear understanding of the requirements and setting clear expectations from the start is important.
No project can succeed without the support and approval of the organization's leaders. Information security needs to be approached from the top down. If employees see that management does not prioritize security, they are unlikely to take it seriously.
A gap analysis, which compares your current security measures with the requirements of ISO 27001, is a helpful first step for any implementation project. After identifying the main gaps, you can create a plan of action that focuses on the most important areas first.
The scope of your ISMS can cover the whole organization, specific departments, or certain locations. The key is to consider the overall situation of your organization and how the ISMS fits within it. When defining the context of your ISMS, you should think about:
A common way to identify internal and external issues is by using a PESTLE analysis:
Political: such as political tensions that could disrupt supply chains.
Economic: like the risk of a recession that might affect your ability to get necessary equipment.
Sociological: for example, how people might view your use of data.
Technological: including advancements in AI, new types of malware, or outdated hardware and software.
Legal: such as laws related to cybersecurity and privacy.
Environmental: like the effects of climate change on your organization.
The interested parties may include:
Your ISMS needs to fulfill two main requirements:
1. The standards set by the relevant guidelines.
2. Your own information security or ISMS goals.
You should set clear security goals and create a plan to reach them. Additionally, you need to document these goals, share them with others, and regularly check on their progress.
The management framework outlines the steps you need to take to achieve your goals. These steps include:
Continuous improvement is a key requirement of ISO 27001 because the threat environment is always changing. To stay protected, organizations need to stay updated and make changes to their security measures as needed.
You can't manage risks if you don't know what they are. However, ISO 27001 does not require a specific method for risk assessment. It only expects you to choose and use an appropriate process.
This process should set clear rules for accepting risks and for how to carry out security risk assessments. It is also important that the assessments give results that are consistent, accurate, and comparable.
Once you have identified your risks, you need to decide how to handle them. Generally, there are four choices:
Avoid – eliminate the source of the risk.
Modify – put a control in place to reduce the risk.
Share – transfer the risk, such as by outsourcing.
Retain – accept the risk intentionally and provide a reason for that decision.
No matter how you choose to handle the risks, record all decisions along with the reasons behind them. Your auditor will review these during the certification process.
Also, you need to create a Statement of Applicability (SoA) and a risk treatment plan. These documents serve as proof of your risk assessment and the measures you plan to take.
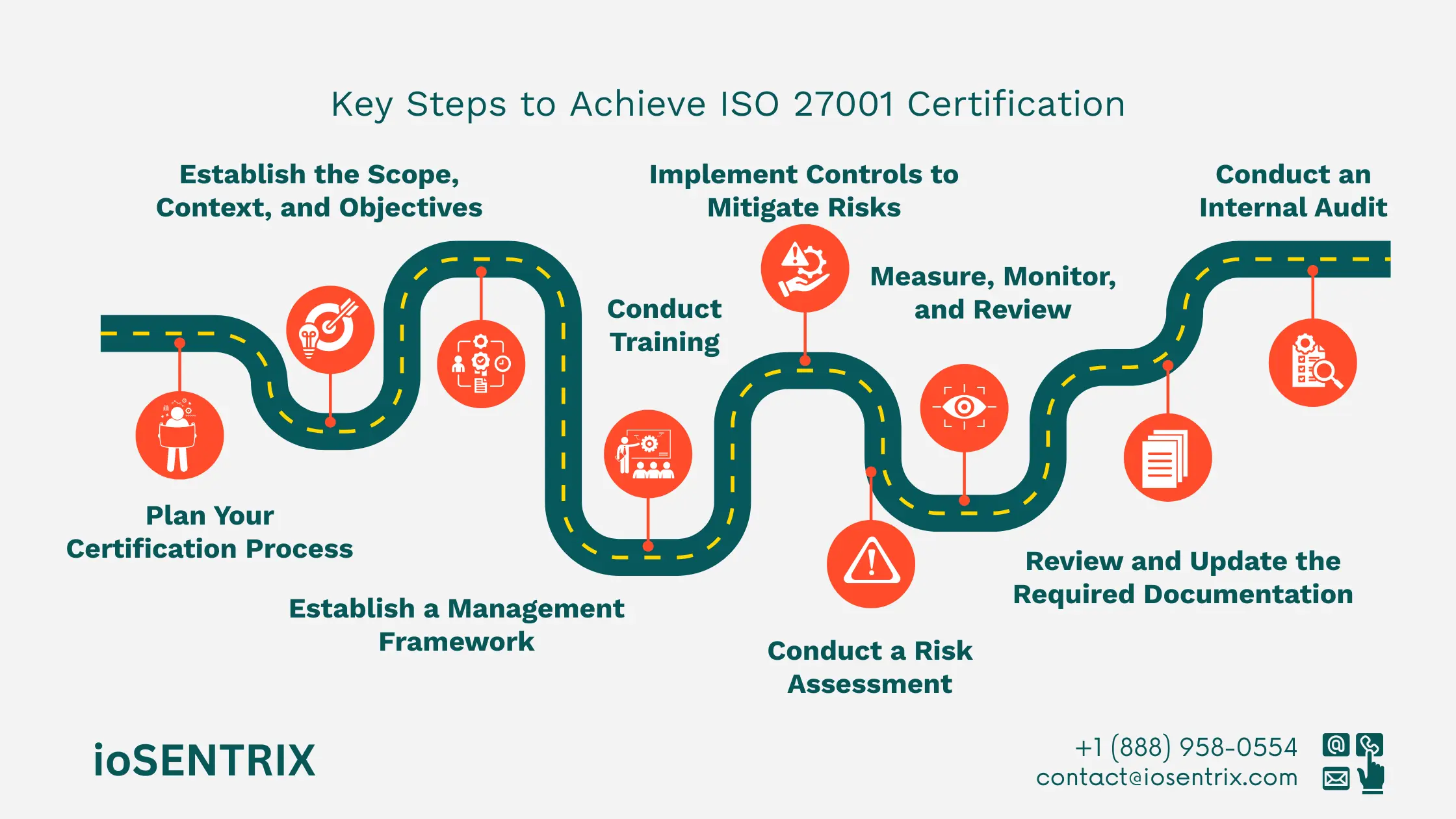
Clauses 7.2 and 7.3 of ISO 27001 specify the need for "competence" and "awareness." The staff responsible for maintaining your ISMS need to have the correct skills to do their work properly.
If there are any skill gaps, you must take actions to fill them. This can be achieved through proper education, training, or gaining relevant experience.
Taking certified training courses can be a helpful way to develop these skills.
All employees and contractors need to be informed about:
Beyond meeting ISO 27001 standards, having alert and aware staff can help prevent data breaches and reduce the risks associated with them.
The Standard often mentions “documented information.” This means that the documents needed for ISO 27001 must meet certain rules:
The first point is clear—if ISO 27001 requires documented information, you need to create it. Also, be prepared for an auditor to ask to see these important documents.
The second point is for your organization to decide. Only you can choose what extra documents your ISMS needs, but keep in mind:
The Standard does not specify a particular format for documentation. Word documents and spreadsheets are usually suitable and work well in many cases. However, there are other formats available that can help make the process faster.
A key part of any ISMS is that it should always be improving. Here is Alan Calder’s view on this, who is a well-known expert in ISO 27001:
“Continual improvement means making better use of your resources. Usually, this involves either:
Basically, you need to review your goals and check how well your performance matches them. Then, evaluate how effectively your ISMS is achieving these objectives, and make changes or improvements if it is not meeting them.
Regular internal audits check the ISMS to confirm it meets the ISO 27001 standards and achieves its goals.
According to ISO 27000, an audit is a systematic, independent, and documented process, which collects evidence and reviews it carefully to see how well the system meets the set requirements.
Although ISO 27001 does not specifically say that the audit process must be documented, the definition suggests that it should be.
ISO 27001 also requires you to create an audit program. This program should include all the requirements for the ISMS, including both the standard's rules and any additional ones you might have.
A certification audit is similar to an internal audit, but it is carried out by an independent registrar that is recognized by its national accreditation body.
(Here is a list of accredited certification bodies for ISO 27001 in the US.)
During the audit, the auditor will check for proof that the ISMS has been put in place, is working properly, and is effective. This may include reviewing items such as:
Certification typically involves two main steps.
The first audit checks if your ISMS has been set up properly and follows the requirements of the standard.
If the auditor finds any issues or nonconformities during this stage, don’t be concerned. This is common, and the auditor will use these findings to help you better understand what ISO 27001 requires and how to meet those requirements.
After the initial audit, you will know which parts of your system are compliant and which areas need improvement. You can then create a plan to make the necessary changes before the final certification audit.
Most minor problems found can be fixed using your corrective action procedures. But if major nonconformities are found, the certification body will probably refuse to give certification until those issues are resolved to the auditor’s satisfaction.
ISO 27001 certification requires not just a well-documented Information Security Management System (ISMS), but also demonstrable, continuous risk management practices.
One of the critical components of this process is the identification, evaluation, and remediation of vulnerabilities that could impact the confidentiality of information assets.
Continuous Scanning and Risk-Based Prioritization: We conduct automated, continuous vulnerability scanning across your network, cloud environment, web applications, and endpoints. These scans identify known security flaws, outdated components, misconfigurations, and emerging threats.
Findings are then classified based on asset criticality and real-world exploitability, not just CVSS scores. This ensures your security team focuses on what matters most, which aligns with ISO 27001’s emphasis on risk-based control selection (Clause 6.1.2).
Remediation Guidance and Tracking: Discovery is only the beginning — ioSENTRIX provides detailed remediation guidance for your environment and technology stack. Our experts help your teams understand why a vulnerability matters, how to fix it, and when to prioritize it.
We also help implement tracking mechanisms that provide an auditable trail of vulnerability resolution — supporting ISO 27001’s requirements for documented corrective actions (Clause 10.1).
Integration with Risk Assessment Frameworks: Unlike traditional scan-and-report services, we integrate vulnerability data into your broader risk assessment framework. Whether you're using ISO 27005, FAIR, or a custom model, technical findings are mapped to business risks and tied directly to your risk register. This bridges the gap between tactical findings and strategic decisions.
Simulated Attacks: Our penetration testing goes beyond automated scans. ioSENTRIX uses manual, targeted techniques that replicate tactics used by real adversaries to assess how well your systems, applications, and network infrastructure can withstand a breach attempt.
This approach identifies vulnerabilities often missed by traditional tools—such as business logic flaws, privilege escalation paths, insecure configurations, and exposed APIs.
Detailed Reporting Aligned with ISO 27001 Risk Treatment Planning: Each test engagement includes a comprehensive report that documents identified vulnerabilities, their potential impact, and how they relate to your information assets and business operations.
We align our findings with ISO 27001’s risk treatment requirements (Clause 6.1.3)—providing severity ratings, recommended actions, and traceable remediation plans that support your organization's risk management processes.
Validate Effectiveness of Technical Controls: ISO 27001 requires organizations to implement a range of Annex A controls—spanning access management, cryptography, system acquisition, and more.
ioSENTRIX’s penetration testing helps validate whether these technical and procedural controls are functioning as intended. This real-world assurance strengthens the credibility of your ISMS and helps demonstrate to auditors that your organization can detect, prevent, and respond to threats effectively.
Secure Code Reviews and SAST/DAST Integration: We conduct both manual secure code reviews and automated Static and Dynamic Application Security Testing (SAST/DAST) to identify flaws such as input validation errors, injection risks, insecure authentication, and other OWASP Top 10 issues.
These services are embedded within your CI/CD pipeline, which enables developers to detect and remediate vulnerabilities early in the SDLC—a key tenet of ISO 27001’s preventive control philosophy.
AppSec Policies Aligned with ISO 27001 Annex A Controls: Our AppSec services are built with direct alignment to Annex A of ISO 27001, particularly:
ioSENTRIX helps organizations formalize and implement secure development policies, enforce change control procedures, and conduct periodic application reviews.
DevSecOps Enablement for SSDLC: Rather than bolting security onto the end of development, we empower teams to build it in from the start. We implement DevSecOps practices that include security testing, code quality checks, secrets scanning, and compliance validations within the CI/CD process.
This continuous, automated approach not only enhances ISO 27001 alignment but also supports a culture of secure coding and accountability.
By aligning these services with the ISO 27001 certification guide, ioSENTRIX helps organizations reduce risks, validate controls, and maintain compliance.
This guide to ISO 27001 certification shows that success requires thorough planning, continuous risk management, and ongoing improvement. Partnering with experts like ioSENTRIX makes it easier to achieve and maintain compliance while strengthening your security posture.
Contact us today to learn how our customized solutions help your organization meet ISO standards, protect your data, and build greater trust with your stakeholders.