What is GIT Source Code Exposure Vulnerability and Why Should You Care?

Cybercrime is still a big concern. While businesses put different technologies to patch the known risk profiles, several new vulnerabilities keep springing up in fact that fresh cyberattacks are recorded every 39 seconds.
That’s not even the end.
Recently, we were researching cybersecurity trends for 2020. We were expecting new threats, but what we found baffled us.
From the findings, we discovered that most web applications are still vulnerable to an old but dangerous security problem; Source Code Exposure vulnerability. In this post, we’ll walk you through, the root cause of this problem, the possible impact it can leave on your business, how to detect it, and finally, show you how to fix it.
What is Source Code Exposure/Disclosure Vulnerability?
For some companies that have built a large amount of intellectual property into their web application, source code is meant to be private. Sometimes the source code also contains sensitive data like secret keys and database passwords, among others.
It’s these confidential data that attackers can use to formulate attacks on your server application.
Now, Source Code exposure vulnerability is when your application cannot protect your sensitive data like intellectual property built in the code, database passwords, secret keys, etc. It usually occurs due to web server misconfigurations or typographical errors in your scripts, like granting executable permissions to specific directories or scripts. Another way we found was using the .git folder that was exposed to the webserver.
What is Git?
Simply put, Git is a Version Control System (VCS) that is mainly used in tracking or monitoring modifications for folders or files during web development. Most webmasters prefer it because of its ‘branches’ feature, which is not only cost-effective but also poses little complications when it comes to managing source code versions.
In as much as Git features and tools like revision, controls are essential in web development phases; every time you initialize Git in any directory, it initiates the creation of local repositories.
The .git repositories, in this case, are .git folders in projects.
They’re the tools that keep track of all modifications on files or folders in your projects. You can lose all your project development history if you delete the .git repositories.
If you leave the .git folder accessible to the public, it gives access to your source code to everyone on the internet who may be able to fetch your intellectual property built into the code, hardcoded credentials if there is any, and discover other logical flaws.
Risk of exposed Git folder
When .git folder is also deployed along with the web application, the attacker could exploit this misconfiguration to download the entire source code along with other sensitive data as explained above.
A publicly accessible misconfigured Git directory will look like this:
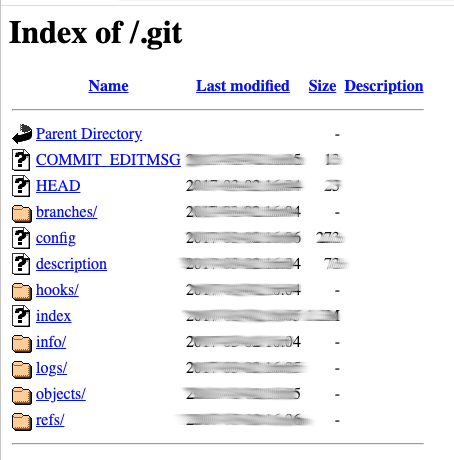
It’s worth pointing out that Git manages the repositories in thousands of small data files or objects. Besides, to keep the data files secret, it also hashes their names to make them hard to guess.
That won’t stop a motivated hacker from trying to access your website’s source code once the .git folder is publicly accessible, though. He’ll still have to find the best means of getting the most of these files.
To stop hackers, the basic rule of thumb is to think like them. Therefore in this illustration, we’re going to use guide-like examples to give you a clearer picture of how a malicious actor could exploit this vulnerability to wreak havoc on your website. We use http://www.example.com for this illustration
There are two ways of achieving this:
1- Using Wget or GitDownloader to Download Git Repository Files
If the Directory listing is enabled on the production server, we will only have to use one simple command to download all the files.
We’ll only run this command
wget --mirror -I .git EXAMPLE.COM/.git/
Once the download is complete, we can view all the status of the entire local changes and compare them with the data we had gotten in the target web server repository as shown below.
1
2
3
4
5
6
7
8
9
10
11
12
/test/xxx.xx (0) (master)
> git status | head -n 15
On branch master
Your branch is up-to-date with 'origin/master'.
Changes not staged for commit:
(use "git add/rm <file>..." to update what will be committed)
(use "git checkout -- <file>..." to discard changes in working directory)
deleted: .buildpath
deleted: .gitignore
deleted: .htaccess
deleted: .project
This status search only shows the deleted files since we only have the .git folder downloaded from the web server. That’s not a problem, though. Running the git checkout -- . command will reset the repository to the last commit.
2- By Analyzing the Standard Files
The only challenge that we might have when accessing the objects here is that they’re all stored as data files. In this case, the git/objects/[First-2-bytes]/[Last-38-bytes]
[First-2-bytes][Last-38-bytes] refers to SHA1-hash of the target object.
1
2
3
4
5
6
7
8
9
10
11
12
> git cat-file -t <SHA SUM>
100644 blob 67045665db202cf951f839a5f3e73efdcfd45021 .gitignore
100644 blob 897dc836601939f72e640ec769775990bf816505 README.md
100644 blob 340ed5b734c078e7828d5e5cda6145731d7b8ca5 firebase.json
100644 blob 9de115f030e3dc9b711202fc5fcc276407223e4e nohup.out
100644 blob 21c08f21e87488b24c6fd25e37ba3e6afab0ac54 package-lock.json
100644 blob 4949d2ded5b21cd894cdb1898b000e4b715b4c4a package.json
040000 tree 18d9667e547f8fc59ab41eacbac136d165e7ca8f public
100644 blob f662648976e2ae816b96be5514e34374072f9695 source.zip
040000 tree 2bce58e64142ea239255af10f48c77731403e416 src
100644 blob 998fb66955909e48d1f2b99b3f048e23c97e7142 yarn.lock
Similarly extracting information from tree type might lead to further trees or blob files.
1
2
3
> git cat-file -p 897dc836601939f72e640ec769775990bf816505
This project was bootstrapped with …..
…….
Or more efficiently we can use automated tools like git-dumper or GitTools that will extract all the available data.
Finally, downloading a specific object doesn’t guarantee that you’ll get all the required data files always. In cases of incomplete repositories, this command will help find all the broken or missing object files: git fsck
What are the Possible Impacts of .git Source Code Exposure Vulnerability?
There are lots of horrifying impacts that this kind of vulnerability can bring on your business. Firstly, an attacker may retrieve your database credentials. He may also extract your API keys, among other sensitive data from the source code if they are hardcoded.
Besides these, the attacker may also use this information to discover even more vulnerabilities which may escalate to more dangerous attacks, which may be unknown to the attacker since the source code wasn’t accessible. These may include database takeovers (using the hardcoded credentials, Time of Check and Time of Use (TOCTOU), and even Remote Code Execution, etc.
How to Detect Server Misconfigurations that could leave your .git Folders Publicly Accessible
From the illustrations above, we’ve seen that the root cause of this problem lies in .git repository vulnerability.
We’ve also seen that it’s straightforward to exploit, especially in websites that host their VCR (Version Control Repository) like (.git/) in the directory listings.
There are two steps to detecting an exposed .git folder:
1- Listing all Web Apps
The purpose of doing this is to find the web app where the .git folder is easily accessible. There are lots of tools that make this process quite fast and easy. A good example is a recon.
In hosting the web apps, you will first enumerate the domains, and focus on the acquisitions.
Tools like Massdns, Amass, or Sublist3r make it even easy to enumerate domains. After the enumeration, browse all your HTTP/HTTPS services to identify all the web apps in use.
2- Detecting .git Exposure via Forced Browsing
After listing all the web apps, you can use forced browsing to find a .git folder accessible on the apps.
It’s simple; go to
Exploit Demo
The videos below provide a demonstration of the exploitation.
How do you fix .git Source Code Exposure Vulnerabilities?
To fix this vulnerability, either remove the git folder from your webserver or ensure that you deny all access to the .git folders.
Listed below is a rundown of quick commands for denying access to .git folders on different servers.
Lighttpd
For Lighttpd, the first step will be enabling this module;
1
mod_accessserver.modules += ( "mod_access" )
From there, you can deny access to the .git folder by adding the following lines to your lighttpd.conf file
1
2
3
$HTTP["url"] =~ "^/\.git/" {
url.access-deny = ("")
}
Apache 2.2
For Apache 2.2 modify the httpd.conf as follows:
1
2
3
4
<DirectoryMatch "^/.*/\.git/">
Order deny,allow
Deny from all
</DirectoryMatch>
Apache 2.4
For Apache 2.4 modify the httpd.conf as follows:
1
2
3
<DirectoryMatch "^/.*/\.git/">
Require all denied
</DirectoryMatch>
Nginx
If you use Nginx, you’ll put this code as the foremost entry in the server-block in your nginx.conf file
1
2
3
location ~ /.git/ {
deny all;
}
Final Word
Cybercriminals are cunning crooks. Detecting and mitigating security risks is never easy unless you’re a certified pen tester or cybersecurity professional who is updated on the latest trends in cybersecurity.
Don’t sit back and falsely believe that your business is small so the hackers won’t target you. They use a plethora of sophisticated tools to mark vulnerable websites, and it may only be a matter of time before a dangerous attack is launched on your servers.
Your help could only be a phone call away. For any inquiries regarding penetration testing, we’re always at your service. Give us a call today or drop us an email and we’ll be glad to give you the best direction.
 Never miss a story from us, subscribe to our newsletter
Never miss a story from us, subscribe to our newsletter