AppSec readiness matters because modern applications face continuous threats across the software development lifecycle (SDLC), requiring security to be embedded into daily development workflows rather than treated as a final checkpoint.
According to Verizon’s 2024 Data Breach Investigations Report, over 74% of breaches involve application-layer vulnerabilities, including insecure APIs, misconfigurations, and flawed authentication logic.
As organizations adopt cloud-native architectures, microservices, and rapid release cycles, security gaps emerge when development and security operate in silos.
AppSec readiness addresses this challenge by aligning people, processes, and technology to reduce exploitable weaknesses before deployment.
Learn more about building secure environments through comprehensive Application Security services.
AppSec readiness is the organizational capability to continuously identify, prevent, and remediate application security risks throughout development, testing, and production.
It extends beyond tools to include secure coding standards, developer training, automated testing, and actionable threat intelligence.
In practice, AppSec readiness includes:
This approach shifts security from reactive remediation to proactive risk reduction.
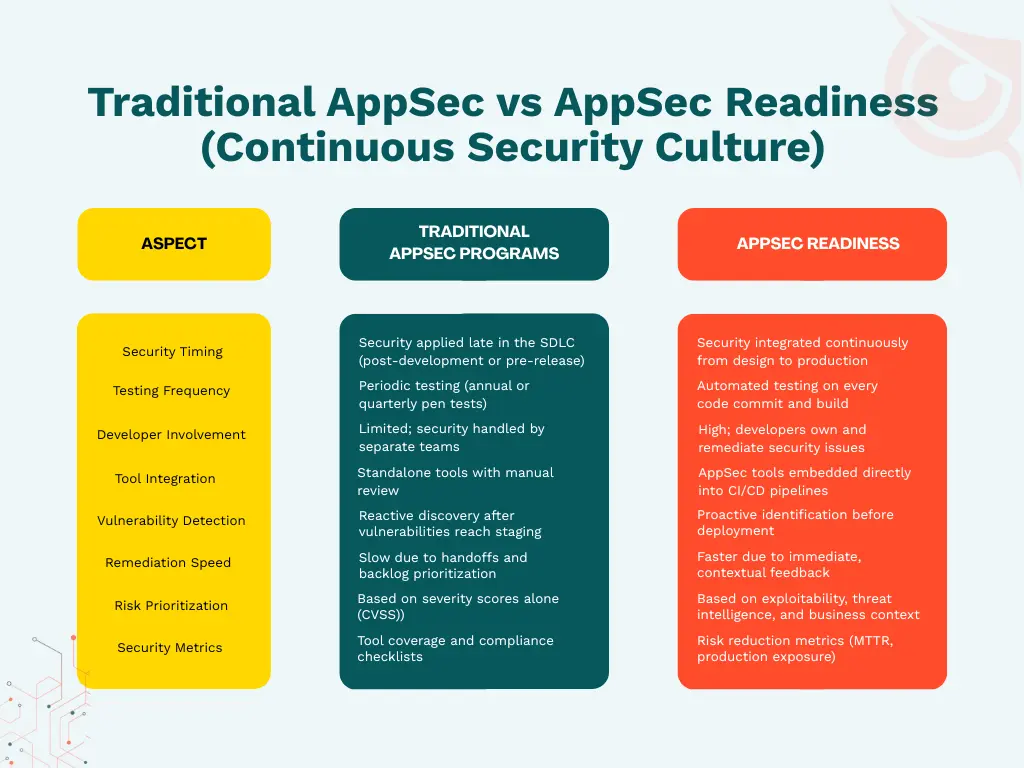
A continuous security culture embeds security responsibilities directly into development teams instead of relying on periodic audits or external assessments.
Traditional models depend on annual penetration tests or post-release reviews, which leave exploitable gaps between testing cycles.
A continuous AppSec culture emphasizes:
According to a 2023 Gartner report, organizations implementing DevSecOps practices reduce critical vulnerabilities in production by up to 60% compared to those using traditional security models.
Developers are the primary drivers of AppSec readiness because most application vulnerabilities originate during coding and design decisions.
OWASP data shows that injection flaws, broken access control, and insecure deserialization consistently rank among the top risks.
To enable developers effectively, organizations must provide:
Empowering developers reduces rework, shortens remediation timelines, and improves overall code quality.
Explore how AppSec adapts to emerging technologies in the agentic AI era.
AppSec tools support continuous security by automating vulnerability detection and prioritization while integrating seamlessly into existing DevOps workflows.
Effective tools focus on accuracy, context, and remediation guidance rather than alert volume.
Key capabilities include:
When combined, these tools provide layered visibility without disrupting development velocity.
Related insights are available in our guide on securing applications in decentralized cloud architectures.
Threat intelligence strengthens AppSec readiness by aligning security controls with real-world attack patterns targeting specific technologies and industries.
Generic vulnerability data often lacks the context required for effective prioritization. Actionable AppSec intelligence includes:
According to IBM’s X-Force Threat Intelligence Index 2024, organizations that prioritize vulnerabilities based on exploit activity reduce breach likelihood by 40%.
Learn how intelligence-driven security enhances protection in AppSec intelligence and threat data.
AppSec readiness is essential for low-code and no-code platforms because abstraction layers can obscure security flaws from traditional testing approaches.
Gartner predicts that by 2026, over 65% of application development will use low-code tools, increasing hidden attack surfaces.
Security strategies must address:
A readiness-based approach ensures security controls adapt to both custom code and abstracted development models.
Read more in our analysis of AppSec for low-code and no-code security.
Organizations measure AppSec readiness by tracking risk reduction metrics rather than tool adoption alone. Meaningful indicators reflect security outcomes tied to development practices.
Recommended metrics include:
These metrics provide objective insight into whether security culture is improving over time.
AppSec readiness strengthens enterprise security by reducing lateral movement opportunities and protecting upstream infrastructure. Application weaknesses frequently serve as entry points for network compromise and data exfiltration.
By integrating AppSec with infrastructure and network controls, organizations create defense-in-depth strategies that address both application and transport-layer risks.
The most important AppSec readiness trends for 2025 focus on automation, intelligence-driven prioritization, and developer-centric security enablement.
These trends reflect the increasing complexity of modern software ecosystems. Key trends include:
Organizations can start building AppSec readiness by assessing current development practices, integrating automated security testing, and establishing clear security ownership within dev teams.
A structured roadmap enables measurable improvements without disrupting delivery.
To evaluate your current AppSec posture and define a readiness roadmap, schedule a consultation with ioSENTRIX.
The primary goal of AppSec readiness is to prevent exploitable vulnerabilities by embedding security into development workflows rather than relying on post-release testing.
AppSec readiness focuses specifically on application-layer risks, while DevSecOps addresses security across infrastructure, pipelines, and operations.
Yes, small teams can implement AppSec readiness by prioritizing automated testing, secure coding standards, and targeted developer training.
AppSec readiness depends more on process maturity and integration than tool cost, with many effective solutions available across budget ranges.